Highlights
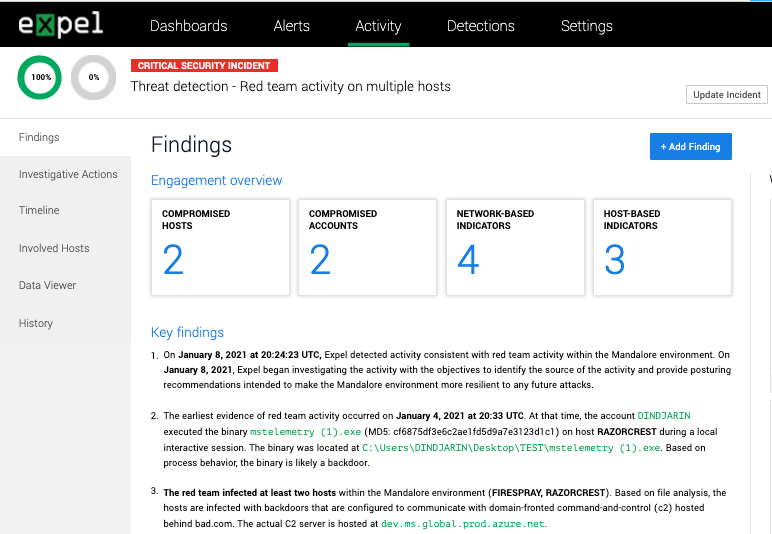
Red team findings report
It’s summertime and the red team season is in full swing. We’ve overhauled our standard finding report and packaged up a new report specific to red team exercises.
Expel provides 9am-5pm support for three business days during a red team exercise. We respond the same way we would if an actual attacker were in your environment. We do a final read-out that includes gaps in your security and recommendations on how to fix them. We also include any changes we’ve made to our detection rules to spot the activity earlier. The new format includes all the details and makes it easy to print and share with others across your organization.
Other enhancements
More EDR support for automated host containment
Last month we announced this new capability with support for CrowdStrike and Microsoft Defender for Endpoint. We’ve expanded our list to include SentinelOne, VMware Carbon Black EDR and VMware Carbon Black Cloud.
Phishing simulations
Sometimes you want your phishing simulation to be a surprise to everyone, including your security team. We made some updates so the next time you run a test, Workbench™ will not ingest these emails. Let your engagement manager know if you’d like to turn on this feature.
Phishing email response
We’ve updated Workbench to send an email response to the end-user after we identify a malicious email. Previously, we notified the user after the investigation was closed. This way, your employees are aware of the status as soon as we have answers.
Other fixes (and a few odds and ends)
- If a secure URL (aka https) is missing while adding a device to Workbench, you’ll receive an error message letting you know to update the field. .
- We noticed GMail and Office365 were sometimes blocking submitted phishing emails from making it to Workbench. Now, after a user submits an email from our phishing button, we’ll encrypt and zip the file so they end up in front of our analysts.
- We resolved a bug that removed some security devices from the Vendor filter on the Security Devices page.