Pumpkin spice lattes (or as some people say, PSL) are back. If you missed the memo, we have a few things in this release to keep you up-to-date. If you’re a PagerDuty customer, you can now receive an automated call or text when an investigation escalates to a security incident. You can also update your settings to receive email notification when we assign new resilience recommendations to your organization.
Highlights
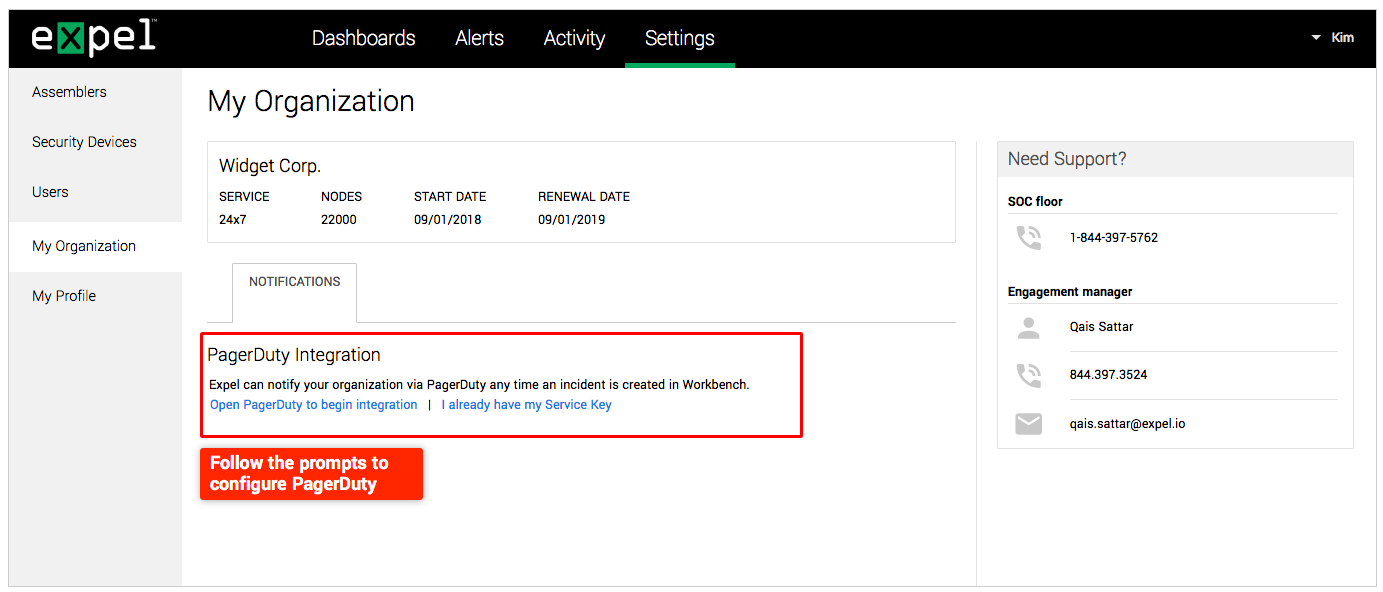
My Organization page
All about you! We’ve added a new page to Workbench. The My Organization page is under Settings and displays information about (you guessed it) — your organization. Details include information about your service, node count, and renew date. You can also find contact information for your engagement manager and the SOC floor. We’ll be adding more configurations and functionality for your organization in coming releases, so stay tuned!
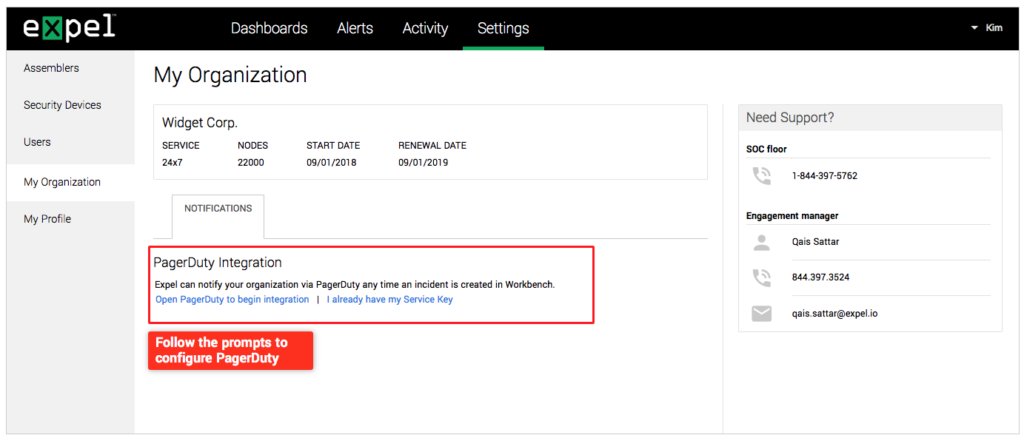
Direct integration with PagerDuty
PageDuty is an incident resolution tool with robust configurations for complex on-call escalations. If you’re a PagerDuty customer, you can configure Workbench to automatically escalate security incident notifications to your PagerDuty account. This integration enables you to automate phone calls or text messages to the appropriate people in your organization. If you’d like support for other notifications, please let your engagement manager know.
To configure PagerDuty, navigate to Settings > My Organization and follow the prompts under the Notifications tab.
Other Enhancements
You’ve got mail. You can now sign up to receive email notifications for Resilience Recommendations. When we create a new recommendation for your organization, you’ll receive an email. To update your preferences, go to Settings > My Profile and click on Edit notifications.
Also, if a Workbench user account is locked or inactive, they will no longer receive email notifications about critical incidents or remediation actions.
Improved investigative workflows for analysts
- We’ve reordered the investigative action elements. They’re now in order of how an analyst would fill in the information. Like putting the start time before the end time.
- If you’re investigating a FireEye HX alert, the Alert ID will pre-populate in the appropriate investigative field.
- Analysts can now select “Cloud” as an investigative option.
Other fixes (and a few odds and ends)
- Analysts can now create a new investigative action for cloud devices.
- We resolved an issue that created parsing errors. The issue was specific to Palo Alto Networks custom rules.
- We’ve updated the descriptive information on Remediation Actions so the context is more useful.
- We fixed a bug that prevented an analyst from being able to add/edit Resilience Recommendation groups.
- We’ve improved our Alerts Analysis Dashboard so devices that cannot generate alerts are not shown.
- We updated the Alerts Analysis Dashboard display for deleted devices. In addition to the device being grayed out, we’ve also added a “Deleted” timestamp.
- We’ve fixed an issue with our email templates. Previously the health message box would appear empty if there was no message to display. It will now no longer show the box.