Expel Managed Security Products
MDR, threat hunting, phishing, & vulnerability prioritization
Improve managed security across surfaces with existing tech and a user-friendly platform.
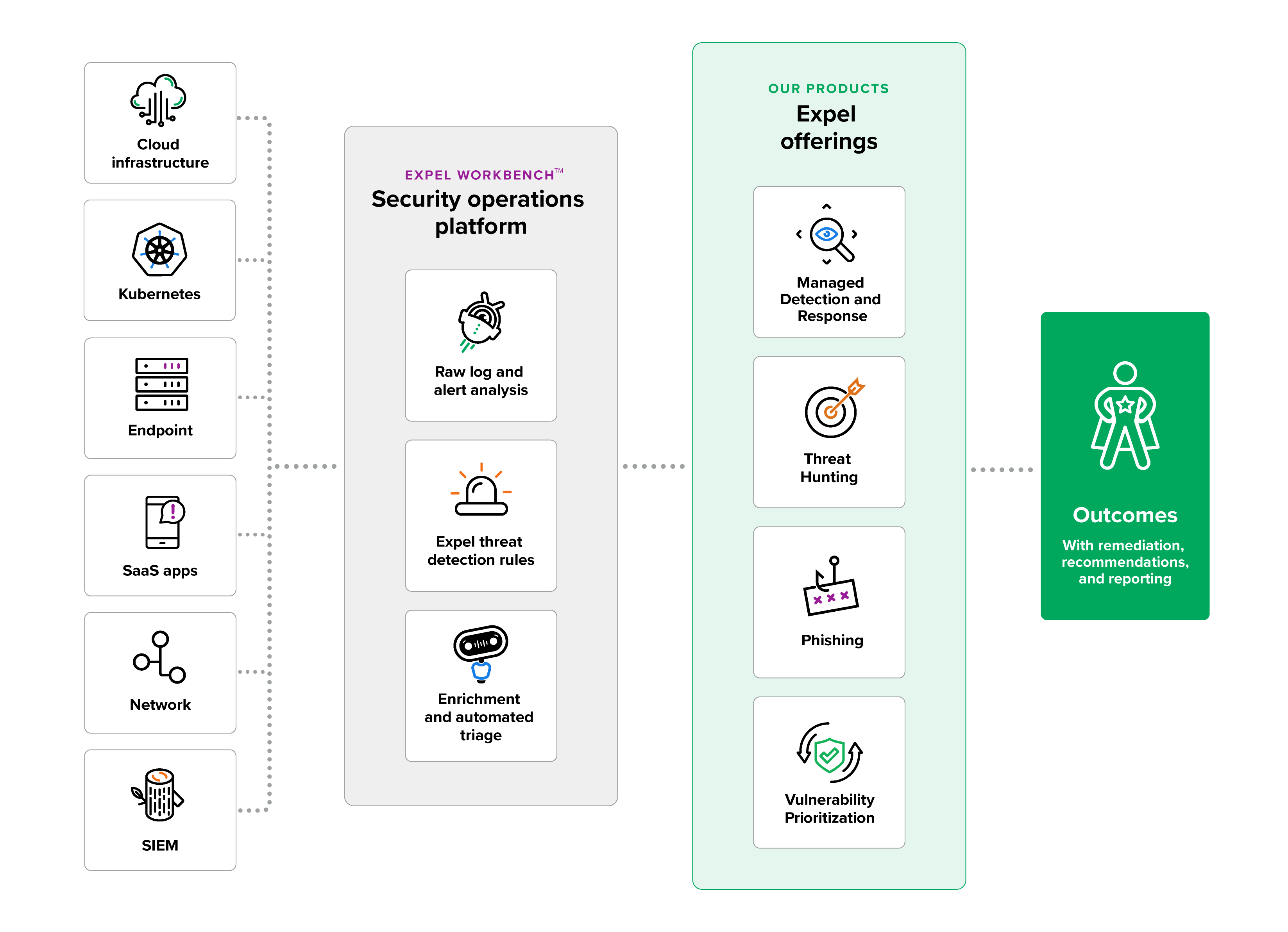
A software-driven approach to managed security
Our security operations platform leverages existing tech to bring together your data across cloud, SaaS, on-prem, network and SIEM to translate alerts into prescriptive outcomes.

Expel’s products
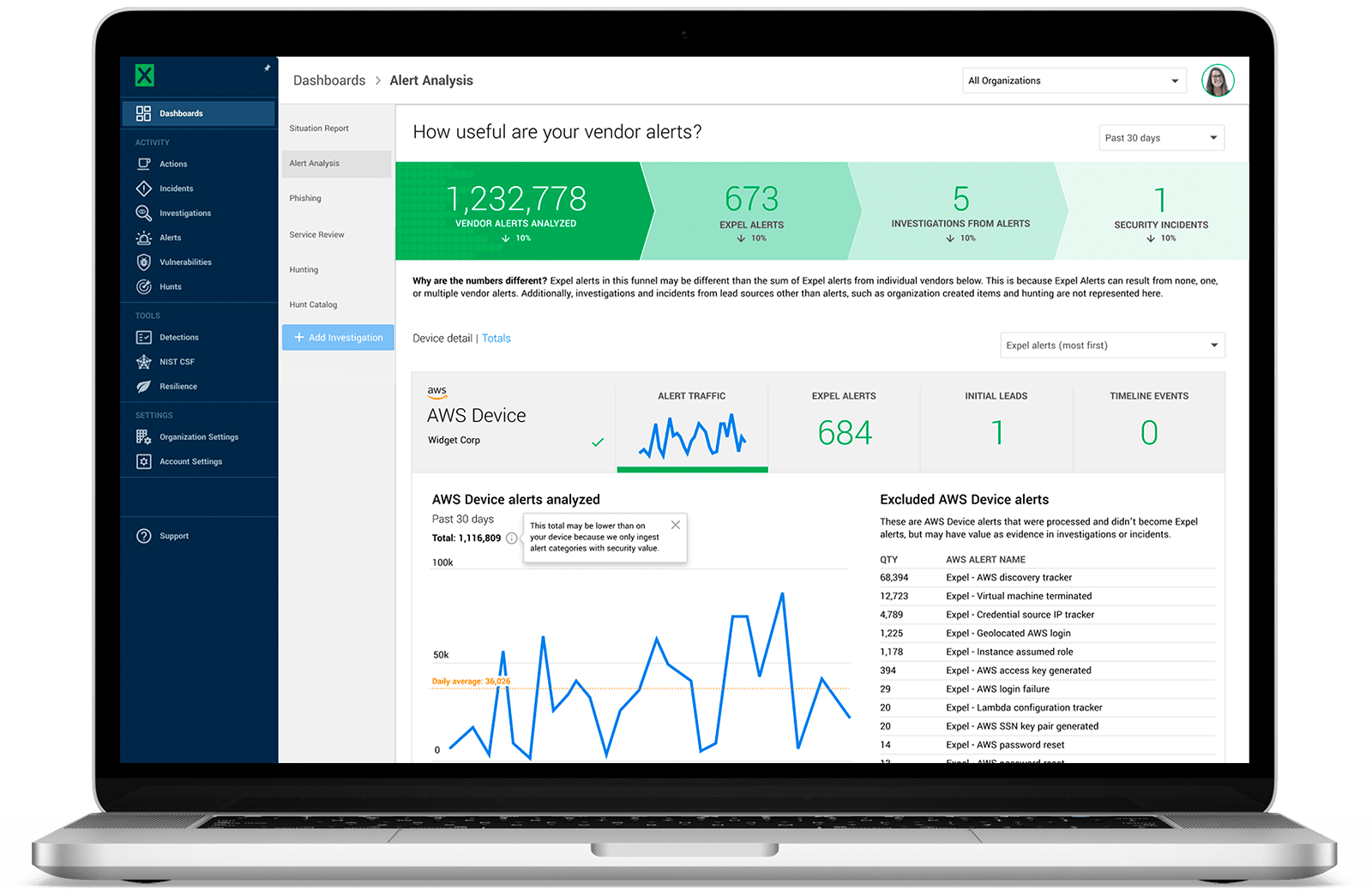
Our products are powered by our security operations platform, Expel Workbench™, which automates alert analysis, prioritization, and remediation so you get answers sooner to what matters the most.
Managed Detection and Response (MDR)
24x7 coverage across attack surfaces to detect, investigate, and remediate risks before they become incidents with full transparency along the way.
- Prioritize detection based on what matters to your business
- Reduce false positives and alert fatigue
- Gain contextualized answers and prescriptive outcomes
Phishing
We triage, investigate, and respond to your phishing inbox, so you can do more without risking business email compromise.
- Automate the triage of reported phishing emails
- Identify which employees may be compromised
- Review trends of phishing attacks to continuously improve
Threat Hunting
Leverage a library of custom-built hunting techniques to detect risks before they become threats — and get clear guidance on how you can improve.
- Proactively hunt for unexpected activity
- Tailor custom hunts to your business needs
- Prevent risks you didn’t see coming
Vulnerability Prioritization
We accelerate your remediation process by letting you know exactly which vulnerabilities pose the greatest risk.
- Automated risk-based prioritization, matching internal context with exploitability
- Dedicated team to investigate and provide guidance
- Integration with the scanner technology you’re invested in
Integrations
BYO Tech
Our security operations platform leverages the tech you already have—there's no additional software or agents to install, letting you decide on the security tools you use now and in the future. Our custom-built threat detection rules continuously learn and apply intelligence across the platform so you always get answers – not just a bunch of alerts. And you’ll benefit from our growing integration portfolio.
View all Expel integrations
Pricing
Get a quote
Whether you’re a Fortune 500 company or a boutique law firm, Expel can help you get better security…overnight. You choose the attack surface you’d like us to monitor and we’ll provide 24x7 detection and response. All services include access to Expel Workbench™, real-time access to our SOC team via Slack or Microsoft Teams and custom recommendations that reduce risk and build resilience.
Request pricing