Expel Managed Detection and Response (MDR)
24/7 decision support for answers, not alerts
MDR that safeguards your cloud, Kubernetes, on-prem, and SaaS environments
How we help
Get answers, not alerts
We provide 24/7 MDR services across cloud, Kubernetes, SaaS and on-prem. Through a software-driven approach, our MDR services eliminate the noise and prioritize what matters to your business — with speed, accuracy and transparency.
How Expel is different
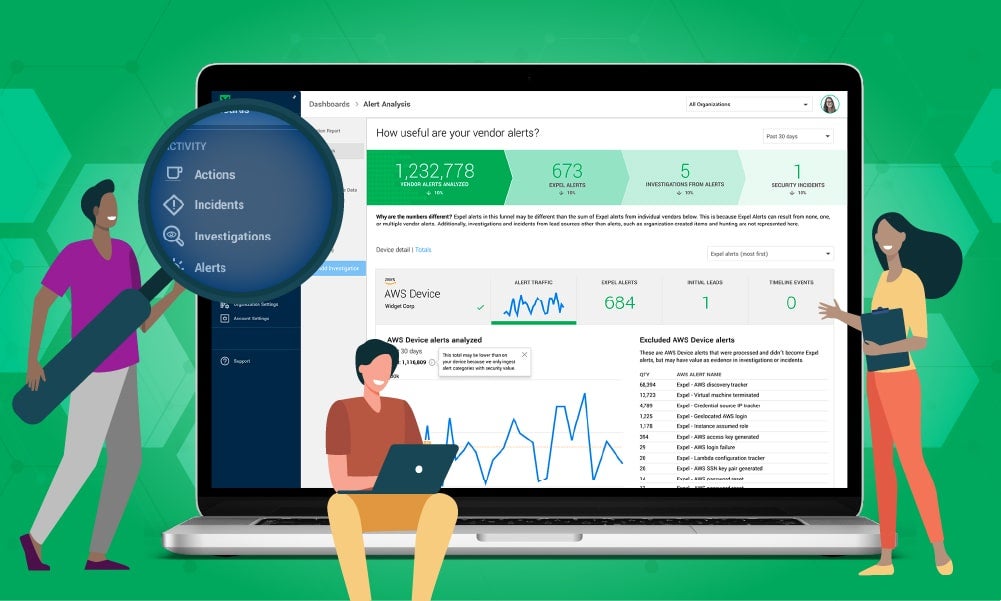
Resolve incidents faster with an automated approach
Our managed detection and response service is powered by our security operations platform, Expel Workbench™. Once you connect your tech, alerts are analyzed by the Expel Workbench platform with an alert review of less than 1 minute. We’ll add context, enrich with intel and assess the risk to auto-remediate or send to an analyst for further investigation. You get the best of both technology and people—all with an average MTTR of only 22 minutes.
Integrate the tech you already have
Connect your tech — no agents, new hardware (or even a SIEM). We’ll apply custom detections and learnings to gain deeper insight and improve ROI.
Get the right automation at the right time
We automate logs, alerts and can auto-remediate on your behalf, or we’ll provide full resilience recommendations for you to resolve.
Filter out noise with context
Our Security Operations Center investigates only the interesting events that require further analysis, so you get immediate answers to the alerts that matter the most.
Get transparency all day, every day
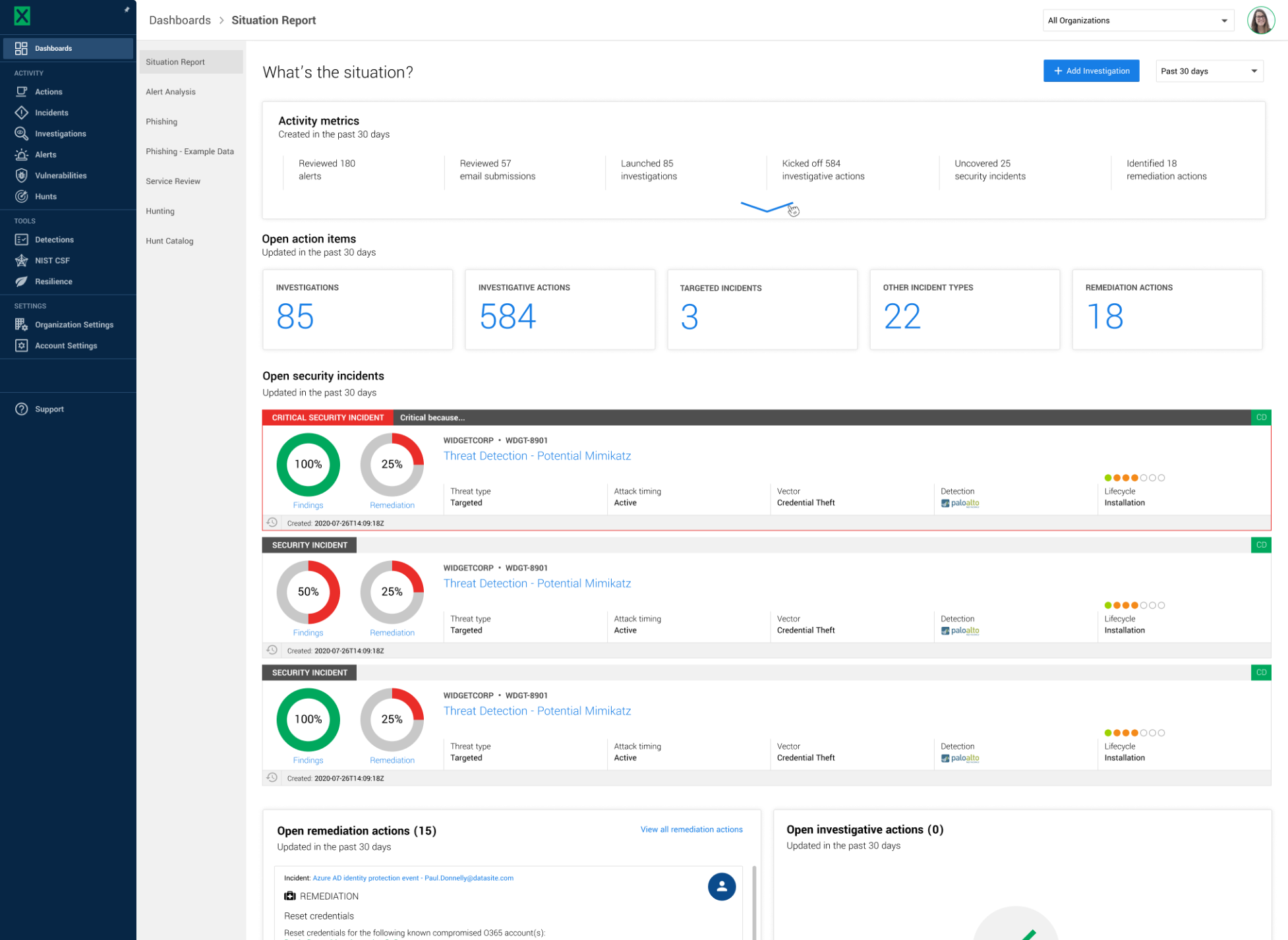
Get complete visibility into the investigation process through real-time alerts when incidents arise and intuitive reporting to prevent the risk from occurring again.
What we offer
24/7 detection and response across attack surfaces
Cloud
Whether you’re cloud-native or migrating, we offer custom detection and response strategies for Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
Secure your cloud infrastructureKubernetes
We’ll integrate with your Amazon Elastic Kubernetes Service (EKS) and Google Kubernetes Engine (GKE) environments to monitor and secure your clusters.
Secure your Kubernetes environmentSaaS Applications
Our custom detections for SaaS applications will give you insight into who’s logging in, from where, and when, across your entire organization.
Secure your SaaS applicationsOn-Prem
Transform your SIEM, endpoint, and network alerts from noise into answers. Our MDR services for on-prem detections spot credential theft, ransomware, hijacking, and more.
Protect against common threats
What you get
Expel MDR
Alert-to-fix timeline with investigation details from initial alert to remediation (and each step along the way)
Expel-written detection rules based on simulated and real-life attacks to continuously improve our MTTR
Threat-specific reporting with attack diagrams, maps, and timelines specific to threats like commodity malware
Response details after our analysts investigate, giving you detailed reports with clear actions
Detailed resilience recommendations with clear guidance on how to improve and get at the root cause of repeated incidents