Protect AWS
Monitor and secure your AWS environment with Expel MDR

Security for AWS … not log chasing
You’ve invested in AWS. It’s incredibly powerful and useful to your strategy. But managing security in AWS is challenging. The logs you get just keep growing exponentially and all you ever seem to have is more questions.
Allocating a number of analysts to review these logs isn’t a practical fix. It’s costly and time consuming… and doesn’t lead to you getting the answers you’re looking for quickly enough.
You know that the faster you know about an incident, the faster you can respond. But with all the alerts and logs to sift through, how can you get there – fast?
What are your biggest AWS protection challenges?
I need to deal with the massive amount of logs and alerts generated by AWS
I need help sifting through AWS security alerts and knowing which ones are real risks
I need help responding to and remediating incidents
I need to maximize my investment in AWS while being secure
Expel MDR for AWS: Results. Not more alerts to handle.
When it comes to AWS we can help.
Our detection approach understands AWS. We’ve learned from countless attacks and our years of expertise enable us to detect threats in your AWS environment, including understanding behaviors, configurations and privileges.
When we notify you about an alert, you can be sure it’s what matters in the context of your environment. We’ve sifted through the noise to serve up the alerts that require your attention. We recommend remediation actions and can remediate on your behalf. We keep pace with all the new (or updated) AWS services as they roll out, so you’re always ahead.
- Reduce risk. Get customized recommendations to secure your AWS environment.
- Maximize ROI. Gain more out of your huge AWS investment, including improved security outcomes without adding new technology.
- Improve security posture. Get proactive recommendations to improve your environment, so you can scale securely.
Our Process
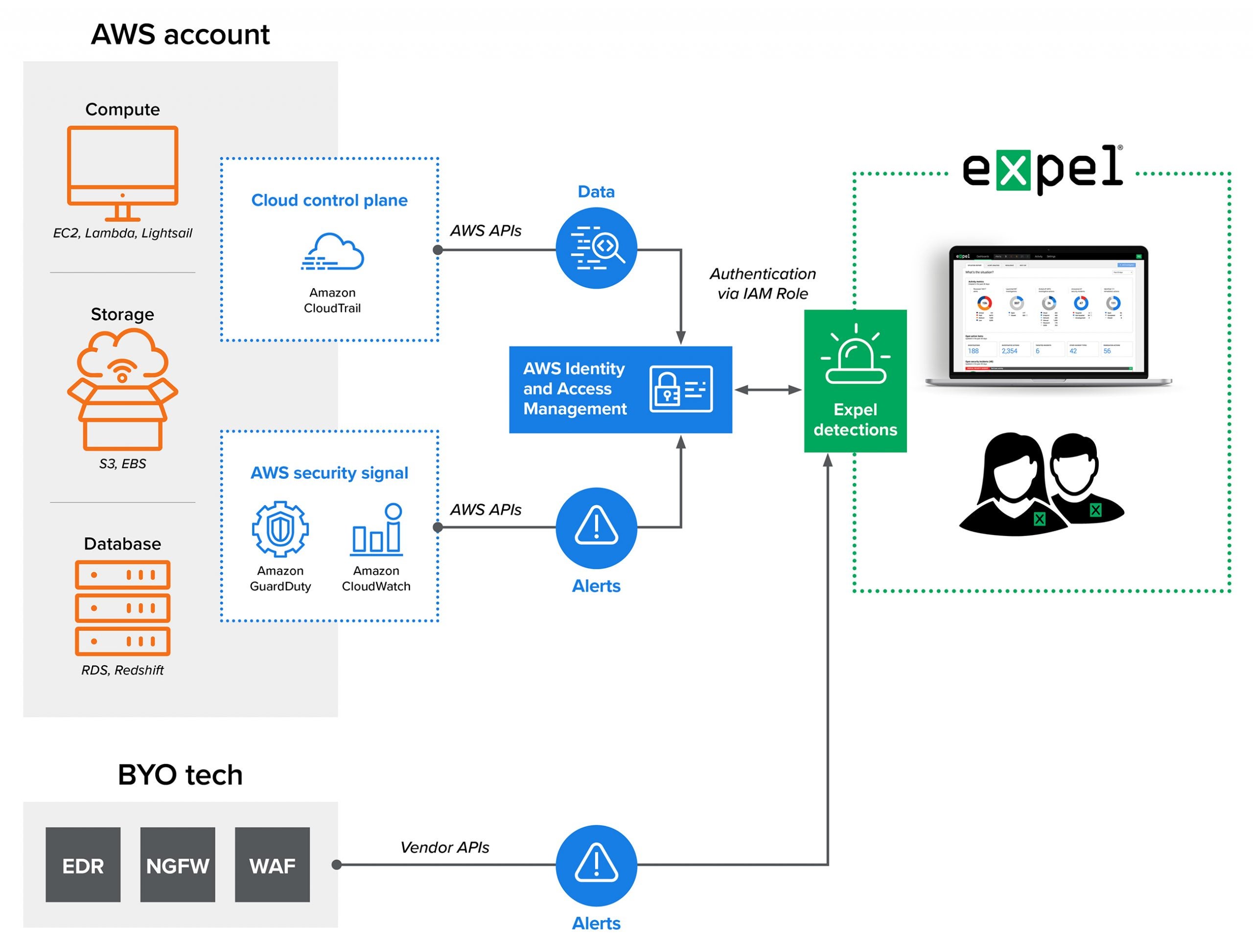
With Expel MDR, we’ll monitor your AWS instance 24×7.
We use API integrations to connect directly with your AWS instance to pull CloudTrail data and alerts from services like GuardDuty and Amazon Inspector. Our bots, Josie™ and Ruxie™, get to work and automatically enrich and triage alerts, surfacing up Expel-validated alerts. Then, we’ll give you step-by-step guides on how to investigate the validated AWS alerts we serve up to you.