Security operations · 5 MIN READ · JON HENCINSKI · AUG 13, 2021 · TAGS: MDR
We’re often asked about the biggest threats we see across the incidents we investigate for our customers. Where should security teams focus their efforts and budgets? To answer these questions, we’re sharing monthly reports on the top attack vectors, trends, and resilience recommendations identified by our Security Operations Center (SOC). Our goal is to translate the security events we’re detecting into security strategy for your org.
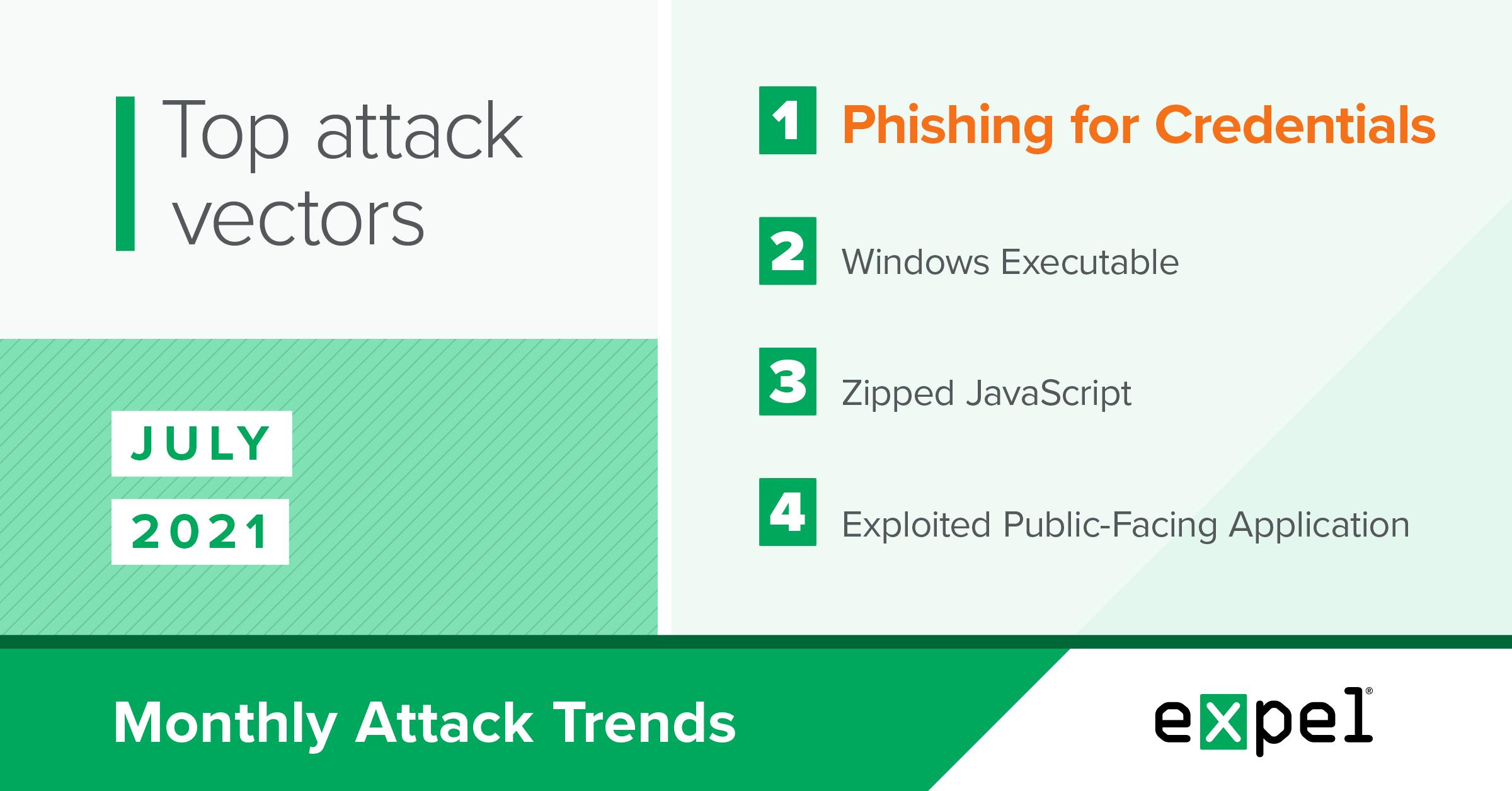
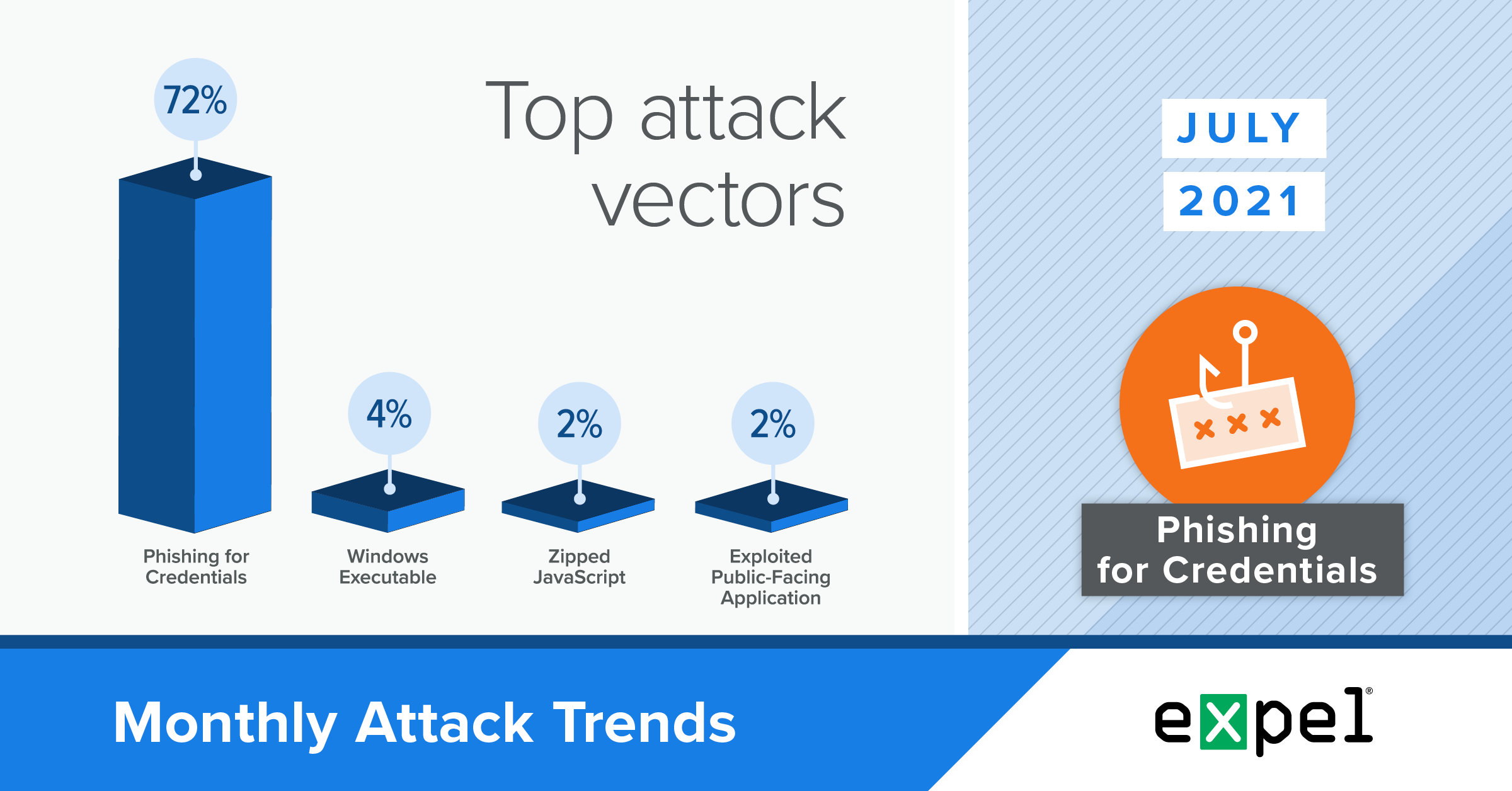
For this report, our SOC analyzed the incidents we investigated in July 2021 to determine the top attack vectors used by bad actors that month. We’ll dive into the trends we’re seeing in two important arenas: phishing and malware.
Phishing
Business Email Compromise (BEC) in O365 is still public enemy number one.
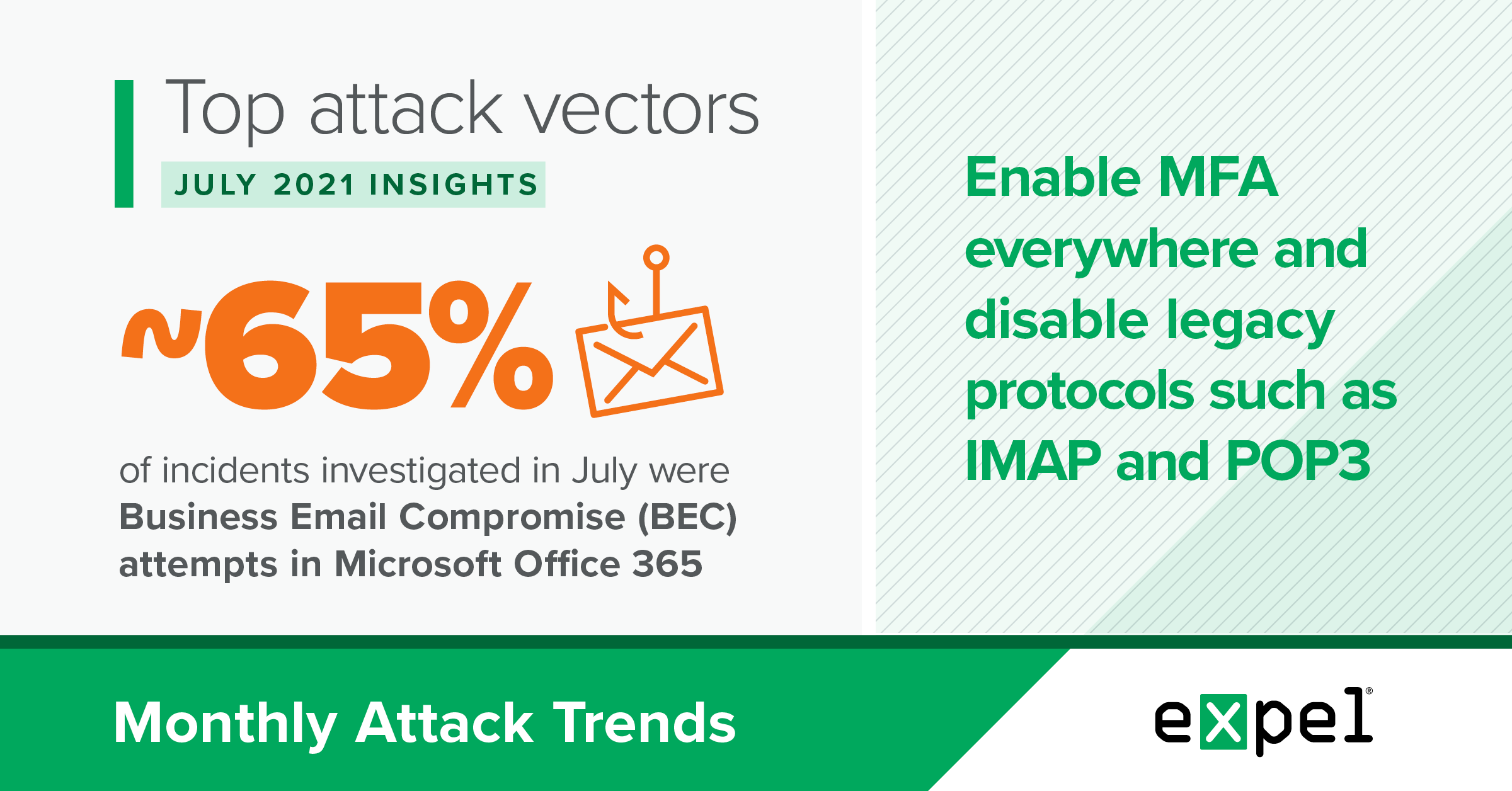
TL;DR: BEC attempts in Microsoft Office 365 (O365) launched from phishing emails were the top threat in July.

Nearly 65 percent of incidents we identified were BEC attempts in O365 – up slightly from June, when BEC attempts in O365 accounted for 53 percent of incidents we identified.
Threat actors behind these campaigns create phishing emails with links to credential harvesting sites impersonating webmail login portals. After the victim enters their credentials, the threat actor can use these credentials to access the victim’s email — potentially opening a treasure trove of sensitive information.
Of note, we didn’t identify a BEC attempt in Google Workspace in July. While Google’s Workspace security settings are pretty straightforward and proficient out-of-the-box, O365 has some initial configurations that must be changed by default to improve security (listed below), otherwise leaving opportunities in play for bad actors.
We expect the trend of O365 BEC attempts to continue and we’re monitoring Microsoft’s plan to do away with Basic Authentication by the end of 2021.
Resilience recommendations:
- Ensure that you’re enabling MFA wherever possible
- Disable legacy protocols like IMAP and POP3
- Implement extra layers of conditional access for your riskier user base and high-risk applications
- Consider Azure Identity Protection or Microsoft Cloud App Security (MCAS)
BEC isn’t just about access to email. Protect your cloud identity providers too!
We’re seeing an increase in the number of attacks targeting cloud access identity providers this year. By attacking these providers, threat actors gain access to SSO credentials and, through them, application data. Nearly 100 percent of the attacks on cloud identity providers we identified in July targeted Okta credentials, a popular SSO technology.
Resilience recommendations:
- Phish resistant MFA (fido/webauthn)
- Enforce MFA prompts when users connect to sensitive apps via app-level MFA
- Customize your Okta sign-in page appearances
Watch out for voice-phishing, aka “vishing”, attacks.
In July, our SOC responded to a remote access scam incident where an employee received a phone call from a scammer pretending to be from the org’s help desk. The employee was instructed to download and install software that allowed the scammer to access and remotely control the employee’s desktop computer. At this point, the employee sensed something was amiss, hung up the phone and contacted their security team directly (good call!). We typically spot these attacks by monitoring for the installation of remote access software that’s atypical for an org.
In these scenarios, the scammer is after credit card information. They typically have the victim deploy legitimate remote access software, then take control of the victim’s computer and give the appearance that their machine is “infected” with “viruses.” At that point, they ask for the victim’s credit card information to “clean up” and repair their machine.
Microsoft recently posted a blog describing a recent ransomware attack that used vishing to gain initial entry.
Resilience recommendations:
- Block installation of remote access software that’s not approved using A/V or EDR.
- Be suspicious of any phone calls received directly from someone claiming to be from your IT Help Desk. It’s totally okay to call them back to verify if it’s legitimate, but make sure to use the help desk numbers provided by your company and not the caller.
- If you notice something suspicious, contact your IT Help Desk or security team.
Malware
Bad actors continue to favor user execution > exploitation
TL;DR: You’re far more likely to experience an incident from an employee unintentionally self-installing malware or running an evil macro than from an unpatched vulnerability.
Deployment of widely distributed commodity malware on Windows-based computers accounted for 17 percent of incidents that we responded to in July. Commodity malware includes “droppers,” programs to steal employee information, coin miners and banking Trojans.
Only one opportunistic malware incident in July was the result of a software vulnerability. The rest? Techniques that required user execution. Examples: Zipped JScript files, Zipped Windows Executables and Microsoft macro-enabled Word documents. These aren’t exploits. This is “feature” abuse.
While we certainly recommend staying up-to-date with the latest OS and software updates, orgs need to evaluate and control the “double click” attack surface.
It’s worth noting that we didn’t identify an incident where malware was deployed to a Google Chromebook or macOS-based computer in July. All of the commodity malware incidents we identified in July involved a Windows-based computer.
We fully expect the trend of threat actors favoring user execution over exploitation to continue.
Resilience recommendations:
- We know disabling Office macros isn’t easy, but it’s worth exploring given their tendency to be exploited
- Consider associating WSH files with Notepad to mitigate common remote code execution techniques
- Disable Excel 4.0 macros
WordPress security and its ecosystem have improved over the years, but it’s still an attack vector.
In July, our SOC stopped a ransomware attack at a large software and staffing company. The attackers compromised the company’s WordPress CMS and used the SocGholish framework to trigger a drive-by download of a Remote Access Tool (RAT) disguised as a Google Chrome update.
In total, four hosts downloaded a malicious Zipped JScript file that was configured to deploy a RAT, but we stopped the attack before ransomware deployment and helped the organization remediate its WordPress CMS.
Keep up to date on patches, but also consider the resilience recommendations below.
Resilience recommendations:
- Run trusted and well-known WordPress plugins
- Follow a WordPress hardening guide or install a WordPress security plug-in
- Explore implementing or updating your website Content Security Policy to block malicious scripts
- MFA everything and all users
- Lock down your dev and staging instances, too (including adding MFA)
- Run an IR tabletop exercise where the initial entry point is your WordPress site
Takeaways
The wave of ransomware news this summer and the growing trend of bad actors deploying malware using techniques that require user execution highlights the need for orgs to guard themselves against future ransomware incidents (see our recommendations here).
That being said, phishing (and particularly BEC through O365) was by far the most frequent threat we investigated in July, and we expect it to remain that way. Preventing BEC and credential harvesting through phishing and “vishing” should be a priority for resilience efforts.
Orgs should stay up-to-date on the latest phishing trends to update their policies and educate their employees when new tactics are at play.
And our top recommendation to protect against BEC in O365 and account takeover? MFA, MFA, MFA.
Then consider taking some of the additional resilience actions we’ve discussed, like disabling legacy protocols, adding extra layers of conditional access and deploying additional security tools like Azure Identity Protection and MCAS.
We’ll be back with insights on August’s top attack vectors. In the meantime, have questions about this month’s data or what it means for your org? Drop us a note.