Security operations · 4 MIN READ · TYLER FORNES · JUN 3, 2021 · TAGS: MDR / Tech tools
The hits (and headlines) just keep coming.
It seems like every week there’s a new story about an organization that’s become the latest victim of a ransomware attack.
When ransomware strikes someone else in your industry, you can’t help but think, “This could’ve just as easily happened to us.”
Looking across our customer base, 12 percent of the incidents we detected by the Expel Security Operations Center (SOC) in April 2021 had the potential to become a ransomware event. These incidents didn’t result in a ransomware event because we stopped them early in the attack lifecycle.
The prospect of a ransomware attack is scary. But the good news is that there are plenty of precautions you can take to make your org as secure as possible and resilient against ransomware.
Targeted versus opportunistic ransomware: What’s the difference?
Whether a sophisticated targeted attack, or a tried and true tactic that dupes users, you should be on the lookout for these two types of ransomware attacks:
Opportunistic attacks
Unlike targeted attacks, which spend time lurking in an environment for weaknesses, opportunistic attacks prey on orgs that are most likely to not have a strong security posture.
These attacks are used to make a quick buck and use cheap tactics like phishing or scanning for and exploiting common public facing vulnerabilities.
The difference?
A much shorter time to ransom. Once their random attack succeeds, the infection begins and typically spreads very quickly. Similar to targeted attacks, once infected, orgs are forced to exchange money to retrieve their data
We’ve also seen an increase in opportunistic attacks in recent years and our SOC responded to several opportunistic incidents where an actor scanned the internet for remote access services – like Remote Desktop Protocol (RDP) – that are exposed to the internet.
Once identified, the attacker will brute force a weak credential that allows authentication into the server. Then a ransomware payload is uploaded and executed on the machine. This type of attack is often automated and requires no human input to continue to infect thousands of vulnerable machines across the internet.
Since this is a “spray and pray” approach, the goal here is to infect a large number of machines in hopes that a handful of them will end up paying a ransom, instead of targeting and identifying high-value targets.
Targeted attacks
Crafty attackers looking for a big payoff are starting to get more strategic, and are willing to play the long game to get ahold of important data that orgs can’t afford to lose. This means that they’re investing their time in targeting specific orgs (like the healthcare and financial industries) that have the potential to store sensitive data that can draw a large ransom.
Targeted ransomware attacks usually also have a longer time to ransom, where the attacker may have broken in months earlier and implanted themselves into the network using a backdoor. Using this access, they may choose to perform reconnaissance and move laterally to a sensitive server before deploying the ransomware. This guarantees the data that will pay the highest ransom is in control of the attackers.
We’re noticing an increase in targeted attacks – and an increase in the amount of money they’re demanding. In fact, Palo Alto’s recent 2021 ransomware threat report shows that the amount of money attackers demanded in 2020 DOUBLED from the previous year.
Bad actors taking advantage of a terrible and chaotic moment in time? Disappointed but not surprised.
From our front lines, we recently saw a targeted campaign against the financial sector that deployed the GOOTKIT loader via a zipped JavaScript file. Once this payload was delivered, we observed the loader deploy a Cobalt Strike BEACON payload which eventually led to the attempted installation of REVIL ransomware.
This narrative is becoming the standard for ransomware operations and allows for not only the installation of ransomware, but domain reconnaissance, credential theft and any other capability you would expect from a sophisticated actor.
Six things to do right now to guard against a ransomware attack
There are specific actions you can take in your environment today to better protect your org against a ransomware attack:
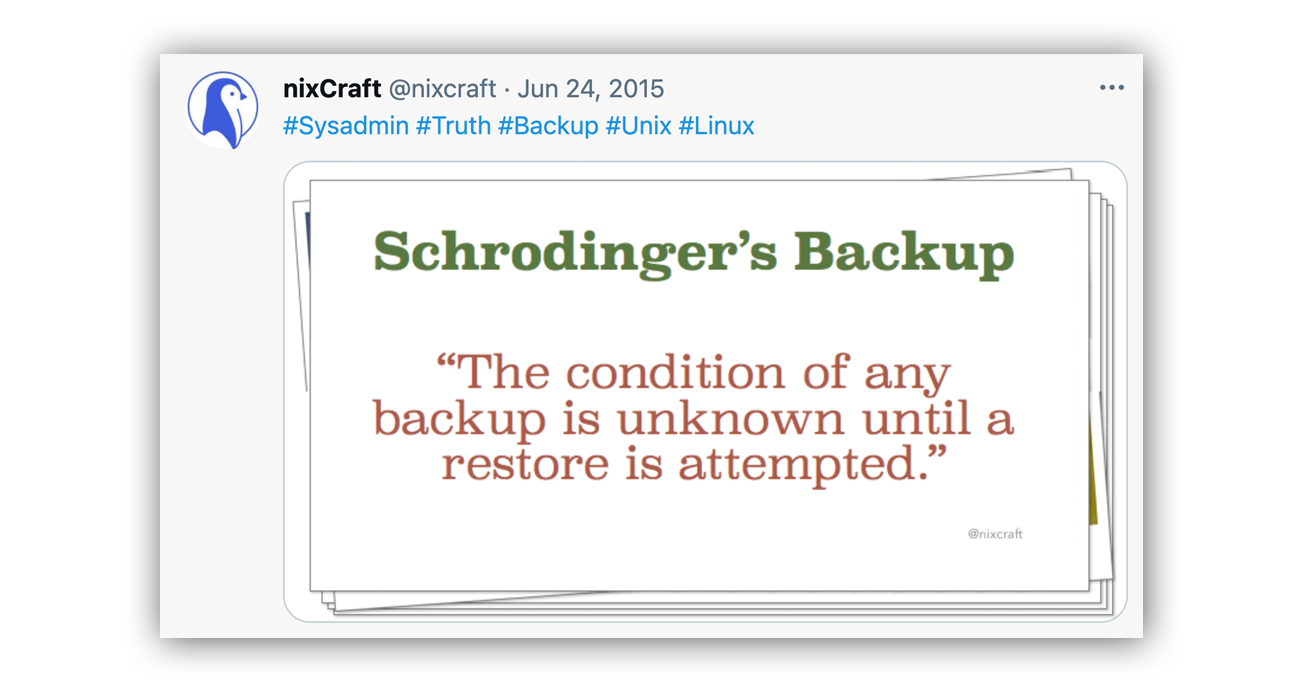
- Create and test backups regularly: Consider creating and testing backups of data within your org as part of your IT policy. Regularly creating valid backups that aren’t accessible from your production environment will minimize business disruptions while recovering from ransomware attacks or data loss. The most important part? Test them. As a wise Tweet once said:
- Test your incident response plan: A real-life security incident isn’t the best time to test your incident response (IR) plan. Give yours the stress test regularly – we recommend once a quarter – to make sure you and your team know what to do when a bad thing happens. Dare I say you can even make IR testing fun. We made it far more interesting by turning it into a game. You can read all about Oh Noes!, our IR tabletop game, and download your own starter kit right here.
- Disable RDP on Internet-facing systems: Don’t expose RDP services directly to the internet. Instead, consider putting RDP servers or hosts behind a VPN that’s backed by two-factor authentication (2FA). Want to know if you have RDP exposed in your organization? Here’s a Shodan query that can help: port:3389 net:1.2.3.4/24 (where 1.2.3.4 is your public IP space in CIDR notation). If RDP is running on a non-standard port in your organization, adjust port:3389 to the non-standard port number.
- MFA everyone: Multi-factor authentication (MFA) isn’t your silver bullet for stopping a ransomware attack, but it’s still an important part of your security strategy. Add another layer of defense to your org and implement MFA (like Duo or Okta) for everyone.
- Configure WSH files to open in Notepad: Prevent the double-clicking of evil JavaScript files and configure JScript (.js, .jse), Windows Scripting Files (.wsf, .wsh) and HTML for application (.hta) files to open with Notepad. By associating these file extensions with Notepad, you’ll mitigate common remote code execution techniques. Pro tip: PowerShell files (.ps1) already open by default in Notepad. Want to test how these files currently open in your environment? These steps work great!
- Block Microsoft Office Macros: Prevent a user from accidentally running a malicious Office macro. Macros are one of the most common ways an attacker attempts to “trick” a user into running malicious code that can be used to install malware. This is most commonly seen in phishing attacks, where an attacker will send a seemingly legitimate Microsoft Office document for the user to open. This creates an easy vessel for ransomware delivery if macros are allowed across an enterprise. Not sure what your macro policies currently are set to? Check out the Trust Center Settings in Microsoft Office and adjust appropriately for your organization. We recommend:
Better: Disable all Office macros except those that are digitally signed.Best: Disable all Office macros.