Security operations
Security operations | 3 min read
Expel Quarterly Threat Report volume V: authentication bypass vulnerabilitiesThis year, our SOC has already seen 20 severe vulnerabilities identified and exploited. We shine a light on the most dangerous of those vulnerabilities and tell you how to protect your org.
Security operations | 2 min read
Expel Quarterly Threat Report volume IV: suspicious authentication sourcesOur series wouldn’t be complete without an analysis of identity-related incidents. Take a look at some of the attacks our SOC team saw in Q1, emerging trends, and steps to protect your org.
Security operations | 1 min read
Expel Quarterly Threat Report volume III: high-risk malwareNext up in our Q1 QTR blog series, we examine high-risk malware incidents. This quarter, high-risk malware made up 67% of malware incidents. Here’s what our SOC team saw and how to protect your org.
Security operations | 2 min read
Expel Quarterly Threat Report volume II: attackers and AIOur Q1 QTR blog series continues with a deeper look at attackers using AI to enable more sophisticated social engineering attacks. Check out our key findings and recommendations for protecting your org.
Security operations | 1 min read
Security alert: Palo Alto Networks PAN-OS GlobalProtect Command Injection VulnerabilityPalo Alto Networks disclosed that attackers are exploiting a vulnerability in PAN-OS for GlobalProtect. Here's what you need to know.
Security operations | 2 min read
Patch Tuesday roundup for April 2024The April 2024 Patch Tuesday included 150 CVEs from Microsoft and Adobe delivers multiple security updates to address 24 CVEs. Here’s what our team recommends to reduce exploit risk.
Expel insider | 1 min read
Expel clinches Gold at the 2024 Globee® Awards, named Top Cybersecurity Vendor of the YearOur Top Cybersecurity Vendor of the Year honor from the Globee Awards underscores our commitment to securing digital infrastructures and safeguarding businesses against cyber threats.
Security operations | 2 min read
Expel x Google Cloud Next ‘24: pioneering next-gen cloud securityWe’re heading out to Google Cloud Next ‘24 to elevate the discussion around cloud security with cloud visionaries and thought leaders. Will you be there?
Security operations | 1 min read
Security alert: XZ Linux utility backdoorResearchers identified a backdoor into the XZ Linux utility, via supply chain compromise. Here’s what you need to know.
Security operations | 7 min read
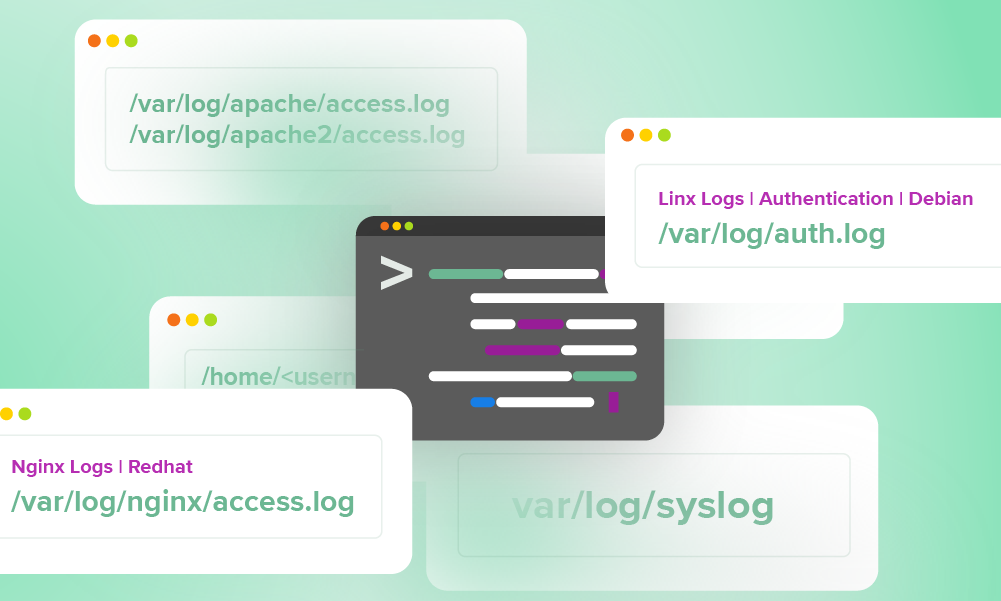
Logs your SOC can use every day: a quick reference guideWe pulled the logs our SOC team use daily into a handy quick reference guide for our analysts—and now, you. Here’s your copy of a helpful log guide to make life easier for analysts.
Security operations | 3 min read
No honor among ransomware criminalsAs the recent drama between the BlackCat ransomware gang and its affiliates shows, there’s no honor among thieves. Take steps to assess your org’s security now, so you can stay out of that kind of mess.
Security operations | 2 min read
Patch Tuesday roundup for March 2024The March 2024 Patch Tuesday included 60 CVEs from Microsoft and a macOS Sonoma Security Update to address 68 CVEs from Apple. Here’s what our team recommends to reduce exploit risk.
Security operations | 8 min read
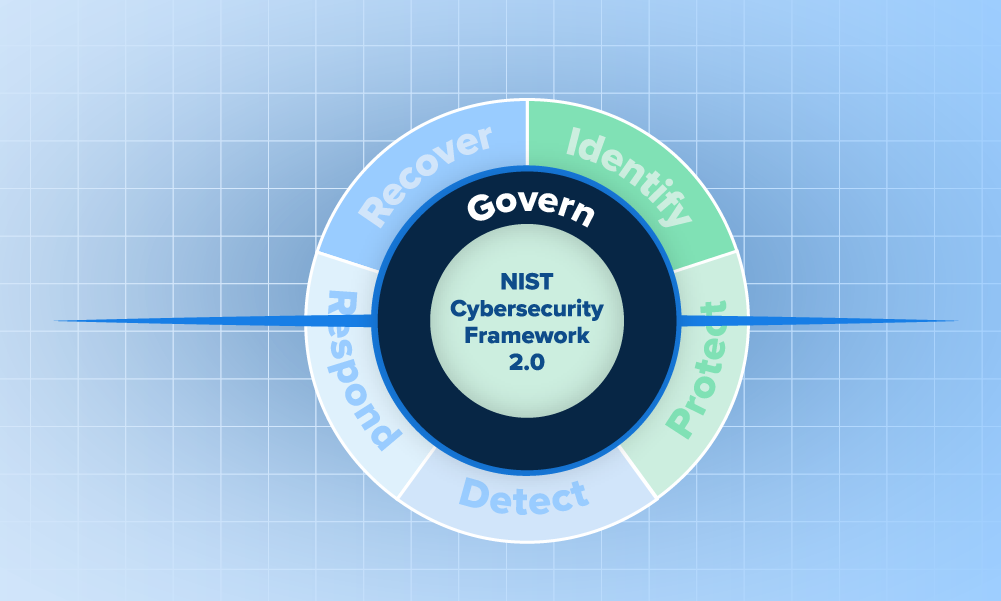
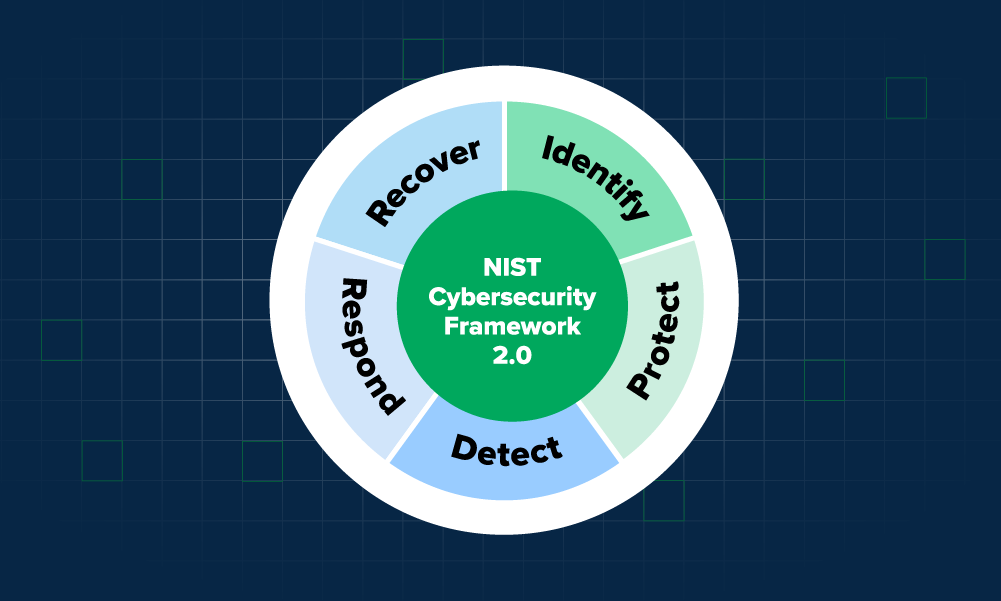
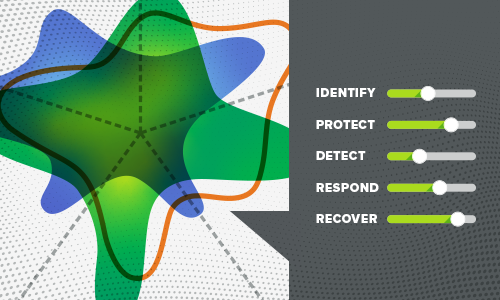
How to get started with the NIST Cybersecurity Framework (CSF) 2.0We give you a quick tour of the NIST CSF and describe how you can baseline your efforts in a couple of hours. So check it out.
Security operations | 2 min read
Security alert: Ivanti Connect Secure and Policy Secure zero-day vulnerabilitiesThe Cybersecurity and Infrastructure Security Agency (CISA) believes threat actors are exploiting Ivanti Connect Secure and Policy Secure zero-day vulnerabilities. Here's what to know.
Security operations | 2 min read
Security alert: ConnectWise ScreenConnect 23.9.8 security fixVulnerabilities affecting ConnectWise versions 23.9.7 and prior leave self-hosted and on-premise ScreenConnect instances exposed to attackers. Here’s what happened and what can do about it now.
Security operations | 4 min read
Automated remediation: benefits and customizationAuto remediation represents substantial benefits, including cost savings and faster response times, but one size doesn’t fit all. Your solution should be customizable for your specific environment.
Security operations | 2 min read
Why is NIST adding Governance to the NIST CSF 2.0?As the security industry waits for NIST CSF 2.0 to publish, you might be asking yourself why NIST is adding more guidance around governance. We shed some light on the question and share what we know.
Security operations | 1 min read
GKE/Gmail vulnerability: notes and tipsSecurity researchers have discovered a new Google Kubernetes Engine misconfiguration. Here’s what you need to know.
Security operations | 7 min read
Transparency in MDR: three use casesTransparency is one of our core tenets. It influences how we built our products, we interact with each other, how we design our compensation systems, and how we work with our customers and prospects.
Security operations | 3 min read
2024 Annual Threat Report: findings and predictionsThis year’s Annual Threat Report describes the major attack trends we saw last year and offers advice to safeguard your org. Some of our top security minds also make predictions for 2024.
Security operations | 3 min read
Let your security maturity be your guideSecurity maturity plays a big role in determining how your SecOps strategy evolves. Learn how an Expel customer determined it was the right time to add threat hunting to his repertoire.
Security operations | 3 min read
New mind maps & cheat sheets: Azure & KubernetesOur new Kubernetes mind map/cheat sheet makes it easier for you to know which API calls are associated with different MITRE ATT&CK tactics in k8s environments.
Security operations | 6 min read
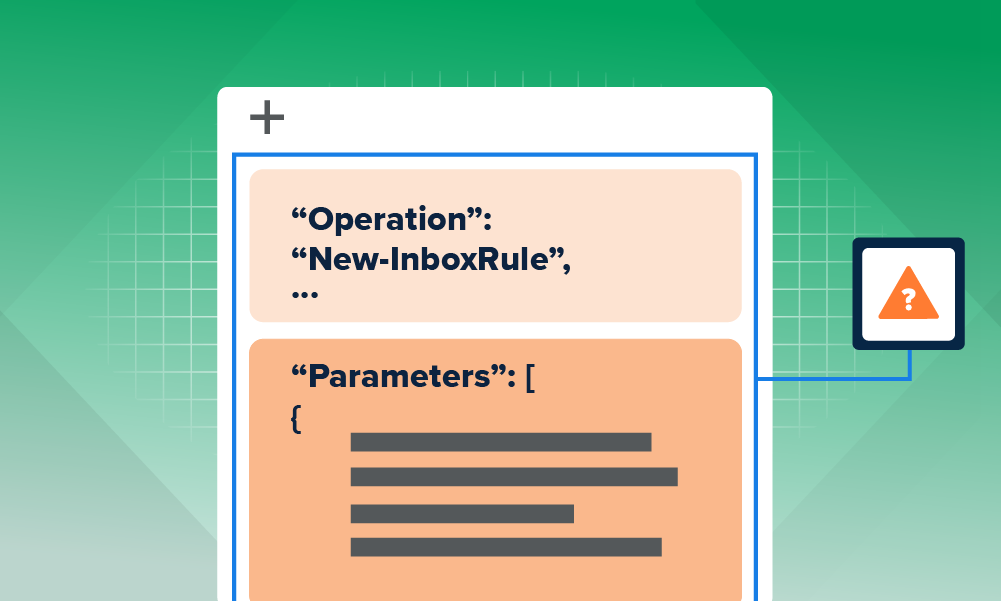
Assessing suspicious Outlook rules: an exerciseOutlook Inbox rules are used for legitimate and malicious reasons alike. Here are some actual case exercises, tips, and tricks on how to analyze them using the rule’s conditions alone.
Security operations | 5 min read
Working with your SOC/MDR during a security assessmentThere are different kinds of security assessments, and what you perform should be aligned to your organization's goals.
Security operations | 7 min read
Attackers are expanding access through Amazon CognitoAWS Cognito provides Identity and Access Management for AWS web applications. Improperly configured Cognito web portals can allow attackers to gain direct access to your AWS control plane.
Security operations | 4 min read
What frameworks and tools drive security maturity?New research by the SANS Institute, commissioned by Expel, outlines the frameworks, tools, and techniques that drive security maturity. Spoiler alert: many orgs are lacking in some important areas.
Security operations | 3 min read
Hackers tattle to SEC: is this a good thing for cyberdefenders?The ALPHV/BlackCat ransomware gang filed an SEC complaint against a victim for not disclosing an attack. They may have won the battle, but it’s possible the stunt will backfire in the long run.
Security operations | 2 min read
Beware this new-ish attacker tactic: QR code attacksThere’s been an increase in “qishing,” the use of QR codes to drive users to malicious URLs in credential harvesting attacks. Here’s what our SOC is seeing plus some insight on how to avoid them.
Security operations | 3 min read
What to expect in NIST CSF 2.0The NIST Cybersecurity Framework 2.0 provides guidance and new tools in areas of governance, continuous improvement, and supply chain risk, plus tools for strategic development and program evaluation.
Security operations | 3 min read
What outcomes can you expect from security-enabled innovation?Security ROI is about a lot more than dollars and cents. The research shows that security investments drive innovation, which has wide-reaching ripple effects that enable business success.
Security operations | 2 min read
Security alert: Okta “support user” data theftOkta recently determined that an attacker stole support system user in an incident identified in October. Here’s what Okta customers need to know and do right now.
Security operations | 4 min read
The clock is ticking: SEC reporting rules hit in DecemberThe new SEC rules for reporting on material cybersecurity incidents go into effect in December. Learn how Expel can help you navigate this process, if your org is affected.
Security operations | 2 min read
Expel Workbench History = unparalleled MDR transparencyManaged security services can often feel like a black box. Workbench's History shows every investigative action in a single thread, from the moment it was triaged through its closure.
Security operations | 9 min read
Beware QR code phishing & other Grinchy scams this holiday seasonAs the holidays approach, cyber Grinches are targeting phishing campaigns to steal data, credentials and more. Look out for these email scams while online shopping and checking your inbox this season.
Security operations | 3 min read
When does an org need to up its cybersecurity game?How do orgs know when or how to up their security game? Every company reaches an inflection point as it grows, and it must have an acceptable level of security to earn customer and partner trust.
Security operations | 2 min read
To build or to buy…that is the questionOne of life’s great questions: should I build my own SOC or partner with an MDR provider? There’s a lot more that goes into the answer than dollars and cents alone.
Engineering | 3 min read
Suspicious Outlook rules: high-fidelity patterns to watch forInbox rule manipulation is hard to accurately alert on since inbox rule creation and management exist for valid reasons. Here’s some tips on how to spot high-fidelity inbox manipulation tactics.
Security operations | 3 min read
Cloud repatriation and cybersecurity challengesMany factors influence the decision to move data and workflows back on-premises. Organizations conducting these migrations must plan for security both during and after the move.
Security operations | 3 min read
Okta cross-tenant impersonation: a new Expel detectionOkta recently described a novel attack on a customer organization. Expel analyzed the information and has developed two new detections for this attack.
Security operations | 2 min read
Risk-based prioritization in vulnerability managementSoftware vulnerabilities are a huge challenge, but risk-based, stakeholder-specific vulnerability prioritization can reduce organizational risk and drive better results. Read the white paper now.
Security operations | 3 min read
Following the lifecycle of a cloud alert in Expel WorkbenchOur new tour shows you the journey a cloud alert takes in Expel MDR for Cloud Infrastructure. It might just change how you think about securing your cloud (or multi-cloud) environment.
Security operations | 3 min read
Staff, C-suite disagree on how security drives innovationThe recent CSA research report found that the C-suite and security staff are disconnected on the role security plays in innovation. We want to explore why that’s happening.
Security operations | 3 min read
Expel Q3 Quarterly Threat Report: the top five findingsThe Q3 Quarterly Threat Report findings are based on incidents our security operations center identified in the third quarter this year. Here are a few of the top trends.
Security operations | 2 min read
Celebrating(?) 20 Years of Patch TuesdayIt’s the 20th anniversary of Patch Tuesday. We can’t patch all vulnerabilities, so we should focus on the ones that are most likely to have an impact on their environment.
Security operations | 2 min read
Oh Noes! Our IR tabletop game is new and improved!Oh Noes!, our incident response RPG, draws games like D&D. You’ll create characters with unique abilities and skills, then role-play cybersecurity incidents specific to your organization.
Security operations | 1 min read
Security alert: privilege escalation vulnerability in Confluence Data Center and Server, CVE-2023-22515A vulnerability in Confluence Data Center and Server allows attackers to create administrative accounts on external-facing Confluence servers. Here’s why it matters and what to do about it.
Security operations | 2 min read
Bridging the risk and cybersecurity gap with Visa and ExpelExpel and Visa have entered into a strategic partnership to utilize MDR for both Visa as a customer and for their clients to mitigate cybersecurity risk.
Security operations | 1 min read
Security alert: zero-day vulnerability CVE-2023-4863 in libwebp (WebP) libraryCVE-2023-4863 is a zero-day vulnerability in libwebp, which can result in arbitrary command execution when exploited. Here’s why it matters and what to do.
Security operations | 3 min read
Proactive threat hunting: the what, why, and howYour threat hunting program should focus on TTPs, holes, and areas of concern around your security posture and create hunts to probe those areas.
Security operations | 6 min read
Wake me up, before you log-log (…or when September ends, whichever comes first)Logs are a necessary and useful component in any cybersecurity practice, but when and how you use them can significantly change your security outcomes.
Security operations | 3 min read
Red team sneakiness: Splunking for AD certificate abuseRecently we saw a red team operation which included attacks against Active Directory, and none of our detections picked them up. Here’s how we solved the mystery.
Engineering | 2 min read
Two new Expel Workbench™ improvements for greater transparencyWe’ve released new features in Expel Workbench that improve transparency. These enhancements give you better visibility into your SecOps today, and what’s in store for the platform in the future.
Security operations | 3 min read
New partner program grows businesses, brands, relationshipsOur approach serves the partner community by helping extract additional value from existing security investments and making them work harder. This way, partners can deliver additional value to their customers.
Security operations | 4 min read
AiTM/business email compromise attacks: what to watch forOne of the most common ways attackers defeat MFA is by using an AiTM credential harvester. Here we outline the most common tactics and provide advice on how to short-circuit this dangerous attack.
Security operations | 2 min read
Cyberattackers evolve: the Quarterly Threat Report for Q2 2023Our Q2 2023 Quarterly Threat Report examines the rise of commodity malware, AiTM phishing techniques, and the impact of new (and old) software vulnerabilities.
Security operations | 2 min read
How MDR complements your SIEM investmentMDR adapts to whatever your SIEM needs to do. Accelerate time-to-value and simplify how you view SIEM security alerts, so that you get the answers you need sooner and more time back for your team.
Security operations | 7 min read
How to identify when you’ve lost control of your SIEM (and how to rein it back in)See if these four telltale warning signs get your head nodding. If so, learn how to get started on regaining control.
Security operations | 8 min read
How much does it cost to build a 24×7 SOC?Not all 24x7 SOCs are created equal. Here we outline four possible security operations centers and an estimate of your costs.
Engineering | 4 min read
The role of artificial intelligence in threat huntingArtificial intelligence—or, more accurately, machine learning (ML)—is a huge boost for threat hunters thanks to its speed, proactivity, automation, efficiency, and ability to promote collaboration.
Security operations | 4 min read
Vulnerability prioritization improves security, saves time & moneyThe best way to reduce your risk profile is to prioritize vulnerabilities based on actual risk. Expel® Vulnerability Prioritization highlights your most critical vulnerabilities so you can fix them first.
Security operations | 3 min read
In the Age of Innovation, Does Security Hold the Key?A new report by the Cloud Security Alliance, commissioned by Expel, showcases the results of research aimed at gaining a deeper understanding of several areas of innovation and cloud use trends.
Security operations | 2 min read
Addressing the new SEC cyber incident disclosure rulesNew SEC rules require publicly traded companies to disclose cyberattacks within four days of determining they’re “material incidents.” We explain what this means and how we can help in that process.
Security operations | 3 min read
How phishing opens the door to business email compromiseBusiness email compromise shares similarities with typical phishing emails, but the two are distinct in some important ways. Understanding the differences is crucial.
Security operations | 2 min read
Threat hunting basics: understanding key principlesThreat hunting basics—continuous monitoring/visibility, intel-driven, hypothesis generation/testing, and collaboration/knowledge sharing—help you detect and smother threats in their infancy.
Security operations | 7 min read
Alert fatigue, burnout, turnover: lather, rinse, repeatMany security orgs are trapped in a difficult cycle. The sheer volume of alerts causes alert fatigue, resulting in service quality degradation and fueling burnout, leading to employees leaving.
Engineering | 1 min read
New Expel Workbench integrations: defend against identity threatsOur latest Integrations with 1Password, Snowflake, Auth0, and Crowdstrike Falcon Identity Protection help protect against identity threats.
Security operations | 2 min read
Risk-based prioritization is the key to your vulnerability management challengesInstead of wasting resources on low-risk vulnerabilities, vulnerability prioritization identifies, prioritizes, and remediates based on relative risk.
Security operations | 2 min read
Threat hunting complements MDR for a stronger defensive strategyAn elite MDR operation works hand-in-hand with a threat hunting team that can jump into an investigation and rapidly uncover critical insights the MDR team can act on immediately.
Security operations | 1 min read
Security alert: critical Fortigate remote code execution vulnerabilityFortinet released a patch on June 9, 2023 for a critical vulnerability in Fortigate Firewalls. Here’s what happened, why it matters, and what you can do right now to reduce risk for you and your org.
Security operations | 3 min read
Security alert: MOVEit Transfer exploited vulnerabilityAttackers are exploiting a vulnerability affecting all MOVEit Transfer versions to exfiltrate data and deploy ransomware.
Security operations | 2 min read
Top three findings from Q1 2023 Quarterly Threat ReportHackers prefer the tried and true. As long as existing methods are working, they’re satisfied. Expel’s Q1 Quarterly Threat Report indicates too many of the existing methods are still working.
Security operations | 2 min read
Vulnerability management, prioritization, and assessment: what’s the difference?Vulnerability management encompasses the vulnerability handling lifecycle. Vulnerability prioritization assigns a level of importance to vulnerabilities based on their potential impact.
Security operations | 4 min read
Expel rides a WaveExpel has been named a Leader in The Forrester Wave™: Managed Detection and Response, Q2 2023. Expel achieved the highest score in the Current Offering category at 4.6.
Security operations | 3 min read
Customer context: beware the homoglyphHomoglyph phishing attacks seek to trick defenders by using URLs with characters that look like valid ones, but aren’t (ạ instead of a). Automation is far more effective in detecting these attacks.
Security operations | 2 min read
Add context to supercharge your security decisions in Expel WorkbenchDefenders need so much information to make good security decisions in the SOC. Adding Context to Expel Workbench is one way to make faster and better decisions.
Security operations | 3 min read
Companies with 250-1,000 employees suffer high security alert fatigueIT decision-makers in the UK say alert fatigue is disrupting workers’ private lives, driving burnout and staff turnover. Companies with 250-1,000 employees are being hit especially hard.
Security operations | 3 min read
Introducing Expel Vulnerability Prioritization: our new solution for helping identify the highest-risk vulnerabilitiesExpel Vulnerability Prioritization triages and investigates unresolved security issues to identify the vulnerabilities that are putting customers at the highest level of risk
Security operations | 3 min read
New UK cybersecurity report: top 5 findingsExpel’s new survey of UK IT decision makers reveals the primary concerns facing both security leaders and front-line workers.
Security operations | 4 min read
An easier way to navigate our security operations platform, Expel WorkbenchOur security operations platform, Expel Workbench, got a makeover to make it easier for defenders to get what they need to protect their orgs even more quickly and intuitively.
Security operations | 2 min read
Security alert: 3CXDesktopApp supply chain attackA supply chain attack on the voice and video conference software, 3CXDesktopApp, has the potential to turn 3CX installers into malicious tools for attacks. Here’s what happened and what you can do.
Security operations | 2 min read
Which flavor of MDR is right for your org?Clear up your MDR confusion with the Gartner® Market Guide for Managed Detection and Response Services.
Engineering | 3 min read
Integrations roundup: new integrations to manage overall business riskExpel has always used a bring-your-own-tech approach to security operations. Now our integrations are expanding beyond the sphere of cybersecurity and into some of today’s most popular business apps.
Security operations | 2 min read
How we spotted it: A Silicon Valley Bank phishing attemptWe’re starting to spot counterparty fraud attempts in the wake of SVB’s collapse. Learn how we spotted one attempt through a custom detection.
Security operations | 4 min read
The SOC organicMDR should be organic, which means integrating the best available automation tech with the experience and insight of analysts who’ve been there, done that, and understand what customers need.
Security operations | 2 min read
Security PSA: SVB collapse presents ripe opportunity for counterparty fraudFollowing the collapse of Silicon Valley Bank and the resulting uncertainty, the opportunity for cyber fraud is massive. Here’s why it matters and what you can do now to protect your org.
Security operations | 3 min read
Kubernetes security: what to look forIf your org does application development, Kubernetes is part of the future. What should you look for when building or shopping for a Kubernetes security platform? Here are a few suggestions.
Security operations | 3 min read
Why MDR for Kubernetes environments is great news for your orgThis post discusses how managed detection and response (MDR) for Kubernetes environments helps organizations relying on in-house application development.
Security operations | 2 min read
2023 Great eXpeltations report: top six findingsOur second annual Great eXpeltations report details the major trends our security operations center (SOC) team saw in customer environments last year. It also offers insights and advice to help you avoid these threats.
Security operations | 1 min read
Understanding the 3 Classes of Kubernetes RiskThe first step toward securing Kubernetes environments is understanding the risks they pose and identifying the ways in which those risks can be mitigated.
Security operations | 2 min read
Tell Dr. Kubernetes where it hurtsKubernetes is growing rapidly, and for important reasons. Like many new technologies, though, it faces growing pains. In part 1 of a series, Dan Whalen outlines the most common Kubernetes challenges.
Security operations | 5 min read
Incident report: stolen AWS access keysHere we walk through what happens when attackers steal a set of AWS access keys. Recently, our SOC, threat hunting, and detection engineering teams collaborated on such an incident.
Security operations | 3 min read
Emerging Threat: CircleCI Security IncidentExpel is aware of CircleCI’s reported security incident and recommendation to rotate all credentials. Here’s what happened, why it matters, what we’re doing, and what you should do.
Engineering | 1 min read
So long, 2022! Our year in reviewTo mark the end of 2022 and the beginning of 2023, we’ve curated some of our favorite blog posts from the past 12 months.
Security operations | 4 min read
Dr. Strangelog or: How I learned to stop worrying and love alertsWhat if your data were higher in fidelity and context? We afford more refined alerts and embed more context and stability, assuming the tech is advanced enough to generate rich security signal.
Expel insider | 3 min read
Touring the modern SOC: where are the dials and blinking lights?SOC tours at Expel aren’t about showing off blinking lights and racks of equipment. Instead it's a discussion about mission, mindset, operations management, results, and demos that make our SOC “go”
Security operations | 3 min read
Expel Quarterly Threat Report Q3: Top 5 takeawaysOur third quarterly (Q3) threat report is here and it’s overflowing with cybersecurity data, trends, and recommendations to help you protect your organization. Here are our top five takeaways from Q3.
Security operations | 4 min read
Attacker-in-the-middle phishing: how attackers bypass MFAA new credential phishing tactic–called “attacker-in-the-middle”–can be effective at end-running MFA defenses. This analysis describes AitM and provides helpful advice for defending against it.
Security operations | 2 min read
Security alert: high-severity vulnerability affecting OpenSSL V3 and higherThe OpenSSL Project has identified two security vulnerabilities affecting OpenSSL v3.0 and later. Potentially affected users of versions 3.0.0-3.0.6 should upgrade to v3.0.7 as soon as it is reasonable to do so.
Security operations | 4 min read
Who ya gonna call (to make the most of your SIEM data)?Customers who import their SIEM to a tool like Workbench can translate all the hours invested in development into customized rules. In other cases, they may realize they no longer need a SIEM.
Security operations | 5 min read
Understanding role-based access control in KubernetesUnderstanding authorization is critical to knowing how role-based access control (RBAC) works for securing Kubernetes. No matter your skill level, you must understand the rules that govern Kubernetes.
Security operations | 3 min read
Three Kubernetes events worth investigatingMonitoring your Kubernetes environment is important — especially if you’re running production workloads. This post explains what you should be looking for once you’ve collected the audit logs.
Security operations | 3 min read
Kubernetes: the whale in the roomMore than half our cloud customers use Kubernetes (k8s), which can help companies ship software faster, avoid platform lock-in, and reap cost savings from elastic infrastructure that scales on demand.
Security operations | 2 min read
Emerging Threats: Microsoft Exchange On-Prem Zero-DaysUntil a patch is issued for the Microsoft Exchange Server zero-day vulnerabilities, there are a few things security teams can do to temporarily mitigate risk. Here’s what we recommend.
Security operations | 12 min read
Detection and response in action: an end-to-end coverage storyThis dramatized case study illustrates how our MDR, phishing, and threat hunting services work, and most importantly, how they work together.
Security operations | 6 min read
Incident report: how a phishing campaign revealed BEC before exploitationBy the time the 89th phishing alert sounded, we knew a large-scale campaign had successfully hit a customer. This case walks you through what happened, what we did, and how it played out.
Engineering | 3 min read
Connect Hashicorp Vault and Google’s CloudSQL databases: new plugin!Expel is excited to open source a new Hashicorp Vault plugin that brokers database credentials between Hashicorp Vault and Google’s CloudSQL DBs.
Security operations | 14 min read
MORE_EGGS and Some LinkedIn Resumé SpearphishingThis post details how we recently detected and disarmed a clever LinkedIn resume spearphishing attack.
Security operations | 7 min read
How we built it: Alert SimilarityOur Alert Similarity tool lets us teach our bots to compare similar “documents” and suggest or recommend a next step, freeing up our analysts. Here’s a walk-through of how we developed it.
Security operations | 3 min read
Top 5 takeaways: Expel Quarterly Threat Report Q2Our second quarterly (Q2) threat report is here and its chock full of cybersecurity data, trends, and recommendations to help you protect your organization. Here are our top five takeaways from Q2.
Security operations | 2 min read
A defender’s MITRE ATT&CK cheat sheet for Google Cloud Platform (GCP)In this new handy guide, we mapped the patterns we’ve seen throughout our GCP incident investigations to the MITRE ATT&CK Framework to help give you a head start protecting your organization.
Security operations | 4 min read
How Expel’s Alert Similarity feature helps our customersWe process millions of alerts each day, and many look similar to one another. We asked ourselves: is it possible to teach our bots to compare similar “documents” and suggest or recommend a next step? (Spoiler alert: YES!)
Security operations | 2 min read
Emerging Threat: BEC Payroll Fraud AdvisoryOur SOC recently observed BEC attacks across multiple customer environments, targeting access to human capital management systems—specifically, Workday. The goal? Payroll and direct deposit fraud.
Security operations | 2 min read
Cutting Through the Noise: RIOT Enrichment Drives SOC ClarityCutting Through the Noise: RIOT Enrichment Drives SOC Clarity
Security operations | 5 min read
Detecting Coin Miners with Palo Alto Networks NGFWWith cryptojacking on the rise, we walk through why we’ve found Palo Alto Networks next-generation firewall is great at detecting it, and some actions we’ve integrated into our detection bot to help.
Security operations | 3 min read
Incident report: Spotting an attacker in GCPIn this report, we walk you through how an attacker gained access to a customer’s GCP environment, our investigative process, and some key takeaways for securing your organization.
Security operations | 4 min read
How Expel does remediationCurious how Expel does remediation? Learn how our process works, what you can expect from our analysts during an investigation and what we’re adding next on our remediation roadmap.
Security operations | 6 min read
Incident report: From CLI to console, chasing an attacker in AWSOur SOC detected and stopped unauthorized access in one of our customer’s AWS environments. Here’s how we spotted it, the steps we took to understand what they did, lessons learned and key takeaways.
Security operations | 5 min read
Attack trend alert: Email scams targeting donations to UkraineAs more people look to donate to Ukrainian relief efforts, bad actors are taking advantage. Lookout for these phishing scams to ensure your donations are actually going to help those in need.
Security operations | 2 min read
Top 7 recs for responding to the Lapsus$ breach claimsWhile the situation surrounding the reported breach of Okta by Lapsus$ is still developing, here are our top 7 recommendations you can take to protect yourself and your org.
Security operations | 8 min read
Top Attack Vectors: February 2022This report dives into the top attack vectors and trends among the incidents our SOC investigated in February 2022. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 5 min read
Evaluating MDR providers? Ask these questions about their onboarding processLooking for an MDR provider? Make sure you understand their onboarding process. Here are the questions you should ask when you’re evaluating MDRs. Bonus: learn how we do onboarding here at Expel.
Security operations | 6 min read
Top Attack Vectors: January 2022This report dives into the top attack vectors and trends among the incidents our SOC investigated in January 2022. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 4 min read
Attack trend alert: AWS-themed credential phishing techniqueThey’re at it again. This time attackers are phishing for credentials by sending fake AWS log-in pages to unsuspecting users. Find out how our crew identified and triaged a phishing email.
Security operations | 7 min read
Top Attack Vectors: December 2021This report dives into the top attack vectors and trends among the incidents our SOC investigated in December 2021. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 4 min read
What’s threat hunting and is it worth it?Heard about hunting but are unclear on whether it’s something you should invest in? You’re not alone. Find out what it is and the value it brings to your org’s detection and response capabilities.
Security operations | 7 min read
Top Attack Vectors: November 2021This report dives into the top attack vectors and trends among the incidents our SOC investigated in November 2021. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 6 min read
Top Attack Vectors: October 2021This report dives into the top attack vectors and trends among the incidents our SOC investigated in October 2021. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 8 min read
A new way to recruit: Our approach to building Expel’s Phishing teamIn this blog post, we’ll share how we’re using the Expel Phishing team and its simple, narrow focus, to achieve two goals -- Protect managed detection and response (MDR) service continuity, and Increase diversity in cybersecurity
Security operations | 5 min read
Top Attack Vectors: September 2021This report dives into the top attack vectors and trends among the incidents our SOC investigated in September 2021. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 4 min read
How we use VMRay to support Expel for PhishingHow does Expel tackle phishing? Smart people and great tech. Learn how VMRay helps our analysts triage and analyze potentially malicious emails submitted by our managed phishing service customers.
Security operations | 5 min read
Top Attack Vectors: August 2021This report dives into the top attack vectors and trends among the incidents our SOC investigated in August 2021. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 5 min read
The top phishing keywords in the last 10k+ malicious emails we investigatedCurious how attackers are prompting victims to engage with phishing campaigns? Check out the top keywords from the malicious emails our SOC investigated and our top resilience recommendations.
Security operations | 6 min read
Swimming past 2FA, part 2: How to investigate Okta compromiseFirst we showed you how to spot an Okta compromise in this two-part blog series. Now we’ll walk you through our investigation and share five tips on how you can strengthen your security defense.
Security operations | 5 min read
Top Attack Vectors: July 2021This report dives into the top attack vectors and trends among the incidents our SOC investigated in July 2021. Learn our key recommendations to protect your org from these types of attacks.
Security operations | 6 min read
How Expel goes detection sprinting in Google CloudBuilding detections in Google Cloud Platform (GCP) but not sure where to start? Time to get strategic. Our detection and response engineers demystify the process for building detections in the cloud.
Security operations | 9 min read
Well that escalated quickly: How a red team went from domain user to kernel memoryA red team recently swooped in and showed off some new tactics. What started as a PowerShell download cradle quickly turned into a custom rootkit download. Find out how we spotted the crafty red team.
Security operations | 5 min read
Incident report: Spotting SocGholish WordPress injectionOur SOC stopped a ransomware attack that compromised WordPress CMS to trigger a drive-by RAT download. Find out what happened, how we caught it, and our recommendations to secure your WordPress CMS.
Security operations | 4 min read
How should my MDR provider support my compliance goals?Need to ensure your tech, privacy and security policies are compliant? Find out what compliance means in practice and how your MDR provider can support your compliance program, not become a liability.
Security operations | 4 min read
Swimming past 2FA, part 1: How to spot an Okta MITM phishing attackCrafty attackers are finding new ways to bypass multiple-factor authentication. Find out how our SOC detected an attack and get some tips on how your org can prevent credentials phishing.
Security operations | 3 min read
Kaseya supply chain attack: What you need to knowA new ransomware attack upheaved the beginning of Fourth of July weekend. Fortunately, there are steps you can take right now to stay safe. Find out what’s happening and how Expel is looking ahead.
Security operations | 7 min read
Come sea how we tackle phishing: Expel’s Phishing dashboardWant a tour of Expel’s Phishing dashboard? Get a behind-the-scenes look at how one of our senior UX designers developed the Phishing dashboard for Expel’s managed phishing service customers.
Security operations | 4 min read
Someone in your industry got hit with ransomware. What now?We’re noticing a trend in ransomware attacks. But that doesn’t mean it’s time to go into panic mode. Find out what you need to know and get some tips on how you can keep your org safe.
Security operations | 8 min read
How to measure SOC qualityYou can scale your SOC and improve quality. Seems impossible? Not if you know how and what to measure. The crew that helped build Expel’s SOC explain how they pulled it off – and how you can too.
Security operations | 7 min read
Cloud attack trends: What you need to know and how to stay resilientWe shared the top attack trend spotted during the pandemic and what to keep an eye out for looking ahead. But how do you remediate and stay resilient against these attacks? Our crew shares some tips.
Security operations | 6 min read
Performance metrics, part 3: Success storiesOur team shares some success stories in creating efficiency and reducing analyst burnout. They end this three-part series with a gift from our SOC – a downloadable resource to measure performance.
Security operations | 3 min read
Expel Hunting: Now in the cloudWe’ve added something new to Expel Hunting: cloud hunts. Find out how our crew’s newly developed hunting techniques can help you spot visibility gaps in your cloud (and give you some peace of mind).
Security operations
The top cybersecurity attack trend we saw emerge during the COVID-19 pandemicCheck out our newest infographic to learn about the top attack trend during the COVID-19 pandemic, how our SOC’s data reinforces these recent findings and how you should be looking ahead.
Security operations | 3 min read
How to make the most of your virtual SOC tourExpel used to give prospects an in-person tour of our SOC. Then 2020 happened. Enter Expel’s virtual SOC tour. Find out what’s included and how you can take full advantage of your time “in” our SOC.
Security operations | 3 min read
Attack trend alert: REvil ransomwareExpel’s SOC spotted a new trend in REvil campaigns and they’re sounding the alarm. Find out what’s new about this type of attack, how our analysts spotted it and what you can do to protect your org.
Security operations | 1 min read
Got workloads in Microsoft Azure? Read thisGot Microsoft Azure? Running Microsoft products in your org? Then you might want to get a free copy of our all-new Azure guidebook.
Security operations | 8 min read
Enhancing phishing protection: analyst & customer securityDiscover how Expel's robust phishing protection measures safeguard our analysts and customers against email threats, providing utmost security and peace of mind.
Security operations | 3 min read
The SolarWinds Orion breach: 6 ideas on what to do next and whyHere are some of our early observations on the SolarWinds Orion breach, plus our ideas on what to do next to detect related activity and better protect your org.
Security operations | 8 min read
How to investigate like an Expel analyst: The Expel Workbench managed alert processEver wonder about how Expel’s analysts investigate alerts? Our SOC team created a workflow called the Expel Workbench managed alert process. Read on to find out how it works and how it can help you.
Security operations | 6 min read
Evilginx-ing into the cloud: How we detected a red team attack in AWSRed team sneak attack? Bring it on. Find out how we tackled a red team attack using open source offensive security tools in AWS and what you can do to protect your org from similar attacks.
Security operations | 4 min read
The CISO in 2020 (and beyond): A chat with Bruce PotterIt’s impossible to sum up a year that felt like 1000 in a single blog post. But we did gather some topline takeaways on security trends and the evolving role of the CISO from Expel’s Bruce Potter.
Security operations | 2 min read
Introducing a mind map for AWS investigationsWe’ve been doing a lot of investigations in AWS using CloudTrail logs and have been noticing some interesting things along the way. So we created an AWS mind map for our team (and you). Check it out!
Security operations | 9 min read
Performance metrics, part 2: Keeping things under controlIn this second post in our three-part series on all things metrics and SOC leadership, our team dives into details of what metrics and techniques are used to protect the SOC against volatility.
Security operations | 8 min read
Why don’t you integrate with [foo]?You’ve heard that Expel integrates with your tech. But not YOUR tech. What gives? Well, sometimes it doesn’t always make sense. Expel’s COO explains why and what this means when working with us.
Security operations | 10 min read
Performance metrics, part 1: Measuring SOC efficiencyHow do you establish metrics for SOC efficiency? This first post in a three-part series shares our team’s approach to setting SOC goals, creating a strategy and measuring success.
Security operations | 8 min read
Is Microsoft Defender for Endpoint good?Expel has integrated Microsoft Microsoft Defender for Endpoint into our platform and we’re impressed! Our SOC analysts share why they love it and how they use it to triage alerts.
Security operations | 5 min read
The myth of co-managed SIEMsThink you can get a co-managed SIEM and then step away to let the magic happen? Not so fast. Our CISO shares some common myths and the realities you should consider before making a decision.
Security operations | 8 min read
Behind the scenes in the Expel SOC: Alert-to-fix in AWSWonder what real-life investigation and response looks like in the cloud? Buckle up! Our team walks you through a coin-mining attack in AWS that they recently foiled – all the way from alert to fix.
Security operations | 8 min read
Spotting suspicious logins at scale: (Alert) pathways to successFind out how our SOC analysts used automation to reduce the time it takes to investigate and report a suspicious login by 75%. The team outlines the process and shares a case study of it in action.
Security operations | 9 min read
Obfuscation, reflective injection and domain fronting; oh my!During a recent red team engagement, the CrowdStrike EDR Platform alerted our SOC team on the execution of a suspicious VBScript file. This is what they learned from untangling the malware code.
Security operations | 7 min read
Managed Detection & Response for AWSLearn how Expel detected and responded to an Amazon Web Services access key crisis with Amazon GuardDuty & CloudTrails logs securing cloud insecurities.
Security operations | 4 min read
Thinking about Zoom and riskFor many of us, Zoom is the app that’s keeping us connected. But recent news about security concerns has a lot of us wondering if it’s too risky. So... is it? Our CISO shares his thoughts.
Security operations | 3 min read
Election security: Why to care and what to do about itWhether you work in security or are an informed voter (or both!), the security of our election ecosystem is everybody’s business. Here are the challenges our system faces and what we can do about them.
Security operations | 5 min read
7 habits of highly effective (remote) SOCsSecurity ops is a team sport … but how do you “play” together when your company’s working 100% remotely? Jon’s got some advice.
Security operations | 2 min read
NIST CSF: A new interactive tool to track your progressThere’s lots to like about the NIST CSF. Here are our practical tips for how to use it, plus a preview of a new NIST feature we introduced in Expel Workbench™.
Security operations | 5 min read
Creating data-driven detections with DataDog and JupyterHubCreating alert thresholds is critical to *not* driving your SOC analysts batty, but what’s the “right” number? Here are some tips, tricks and favorite tools we use to determine alert thresholds for customer environments.
Security operations | 6 min read
Exabeam: an incident investigator’s cheat codeWe love EDR tools too, but here are our best tips and tricks for combining EDR data with other (equally) important security signals.
Security operations | 8 min read
Why the cloud is probably more secure than your on-prem environmentIs your data really safer in the server room next door? Probably not. Here are five reasons why the cloud offers better security than your on-prem environment.
Security operations | 3 min read
Where does Amazon Detective fit in your AWS security landscape?If you’re running workloads on AWS, then you’ll want to know all about the latest and greatest AWS-native security tools. We’ve got you covered in our latest post.
Security operations | 8 min read
Using JupyterHub for threat hunting? Then you should know these 8 tricks.Jupyter Notebook gave us the freedom to rethink the way we analyzed hunting data. Here are some tips and tricks you can use in your own analysis.
Security operations | 5 min read
Making sense of Amazon GuardDuty alertsIf you’re running workloads on AWS, then you’d better be running GuardDuty. But what is it and how can you make sense of all the signals? Here are our pro tips.
Security operations | 5 min read
Better web shell detections with Signal Sciences WAFIs Signal Sciences WAF part of your tech stack? Then you’ve got an amazing webshell detection method right at your fingertips.
Security operations | 5 min read
MFA is not a silver bullet to secure your cloud emailLearn how dual or multi-factor authentication (MFA) are not an entirely secure solution for cloud email security on the Expel blog.
Security operations | 10 min read
Applying the NIST CSF to U.S. election securityNIST isn’t only useful for corporations -- it’s helpful for guiding security activities around processes like our national elections. Our CISO’s got some thoughts on exactly how to apply NIST to election security.
Security operations | 7 min read
Generate Strong Security Signals with Sumo Logic & AWS CloudtrailLooking to get more or better security signals from AWS Cloudtrail? Learn how with Expel.io. See how we use the Sumo Logic SIEM for actionable data.
Security operations | 6 min read
Five things law firms can do now to improve their security for tomorrowRelativity CSO Amanda Fennell shares the top five, easy-to-get-started things she sees forward-thinking law firms doing to improve their security.
Security operations | 8 min read
Our journey to JupyterHub and beyondIf you use or are considering trying JupyterHub, it’s your lucky day -- we’re sharing configuration tips and tricks, how we’re using it to make technical research easier, and much more.
Security operations | 4 min read
3 must-dos when you’re starting a threat hunting programSo you decided you want to build a threat hunting program ... but where do you start? Here are our three must-dos when you’re planning your hunt.
Security operations
Here’s what you need to know about business email compromise (BEC)How often does a business email compromise actually happen? And what should you do about it? Our infographic answers those questions and more.
Security operations | 6 min read
How to make your org more resilient to common Mac OS attacksGot Macs in your org? Here are a few recent Mac OS attack trends and how you can become more resilient to ‘em.
Security operations | 8 min read
The top five pitfalls to avoid when implementing SOARSOAR isn’t really about “orchestration and response.” It’s an engineering problem at its core. Here’s why.
Security operations | 6 min read
How to find anomalous process relationships in threat huntingFinding anomalous process relationships -- commands that don’t belong together -- might indicate a problem within your environment. Here’s how to spot ‘em.
Security operations | 5 min read
This is how you should be thinking about cloud securityYour IT team isn’t racking and stacking servers like they used to, but cracking the cloud security code is easier than you think. Get our pro tips for doing just that.
Security operations | 7 min read
How to choose the right security tech for threat huntingHow do you decide which tech to use to carry out your hunt? This post’s got some pro tips for when and how to use different technology for your threat hunting mission.
Security operations | 4 min read
Don’t blow it — 5 ways to make the most of the chance to revamp your security postureIf you’ve got a blank canvas with the opportunity to build a security program from scratch, here’s how to get started and make the most of your new program.
Security operations | 4 min read
NIST’s new framework: Riding the wave of re-imagining privacyThe NIST Privacy Framework will revolutionize how we think about privacy. Here’s how your org might use it.
Security operations | 3 min read
Four habits of highly effective security teamsPractice these habits consistently and you’ll have an engaged, talented and all-around awesome security team.
Security operations | 4 min read
How to get your security tool chest in order when you’re growing like crazyNeed to expand your security tool chest? Our CISO’s got some tips to consider when thinking about what tech to keep or buy.
Security operations | 4 min read
Does your MSSP or MDR provider know how to manage your signals?How well is your MSSP or MDR going to manage your fleet of security signals over time? Here’s how to figure out whether they’re up for the challenge.
Security operations | 7 min read
How to build a useful (and entertaining) threat emulation exercise for AWSWant to test your analysts’ detection skills in the cloud? Here are our tips and tricks for building your own threat emulation exercise in AWS.
Security operations | 9 min read
12 ways to tell if your managed security provider won’t suck next yearHow can you figure out if the quality of the service you’re about to sign up for will improve over time? Our COO Yanek Korff’s got some tips for making sure you choose a service that’ll last.
Security operations | 4 min read
How to start a cybersecurity program (or restart one that lapsed)If you're left holding the hot potato of a legacy lackluster security program, or are suddenly forced to protect your org and its data with less, here are a few quick steps to take to get cybersecurity efforts back on track.
Security operations | 3 min read
Three tips for getting started with cloud application securityIf you're feeling like your SaaS security knowledge is a bit cloudy, these three pro tips will get you started on the right path.
Security operations | 3 min read
Office 365 security best practices: five things to do right now to keep attackers outHere are five Office 365 security best practices to check out right now.
Security operations | 5 min read
Reaching (all the way to) your NIST 800-171 compliance goalsClose common compliance gaps, without building a SOC, for NIST 800-171 security requirements. And a bit about how we can help.
Security operations | 7 min read
Getting a grip on your cloud security strategyUnderstanding how to think about cloud security differently is half the battle. At Expel, we've thought a lot about it, and we’ve identified three key points that should inform your cloud strategy.
Security operations | 12 min read
A common sense approach for assessing third-party riskLet us walk you through our third-party assessment process. We think it's lightweight but still achieves the objective - determining if a vendor can be trusted. And, as a bonus, we're providing the third-party questionnaire and emails we use so you can download it and get going right away.
Security operations | 7 min read
Lessons learned from a CISO’s first 100 daysIn this guest post, Amanda Fennell, CSO at Relativity reflects on what she’s learned -- I recently finished my first 100 days as Chief Security Officer (CSO) of Relativity. I’ve learned a lot. And while every new CSO faces unique challenges, I’ve come up with some recommendations to help new CSOs.
Security operations | 4 min read
What’s new in the NIST Cybersecurity Framework (CSF) v1.1In case doing a “stare-and-compare” of the original and updated NIST frameworks isn’t your idea of fun, I’ve highlighted three important changes here.
Security operations | 5 min read
What is (cyber) threat hunting and where do you start?We want to demystify what threat hunting is and what it’s not. So here goes nothin’ ...
Security operations | 8 min read
What “I Love Lucy” teaches us about SOC performanceA little nerdy (and a lot math-y) post to help you better understand your SOC's systems, so you know how changes will impact its operation.
Security operations | 5 min read
Managed detection and response (MDR): symptom or solution?An uncommonly clear review of what managed detection and response (MDR) is, where it came from and what it can/can't do for you.
Security operations | 3 min read
Decoded: new changes to NIST’s Cybersecurity FrameworkNIST has polished up their Cybersecurity Framework. Our CISO, Bruce Potter, highlights three of the most significant (and practical) changes.
Security operations | 3 min read
What’s endpoint detection and response (EDR) and when should you care?We cut through the hype to explain what Endpoint, Detection and Response (EDR) products can do for you. (3 min read)
Security operations | 7 min read
Warning signs that your MSSP isn’t the right fitLook out for these 5 indicators that it's probably time to start considering alternatives to your managed security services provider (MSSP). 8 min read.
Security operations | 4 min read
Budget planning: determining your security spendGuidance and a short list of things you can do to help you answer the common question "how much should I spend on cybersecurity?" (5 min read)
Security operations | 5 min read
How to avoid shelfwareSet yourself up for success by asking these four questions before you purchase new security products. (5 min read)
Security operations | 4 min read
Mistakes to avoid when measuring SOC performanceDiscover the three most common mistakes companies make when developing their first set of operational metrics. (4 min read)